Introduction
Feistel cipher is also called Luby-Rackoff block cipher, which is used to construct a symmetric structure of block encryption algorithm. It was invented by the German cryptographer Horst Feistel while working at IBM. Feistel cipher is also called Feistel network.
Many block encryption algorithms are developed on the basis of feistel cipher, such as the very famous DES algorithm.
In feistel cipher, the operations of encryption and decryption are very similar, usually requiring multiple rounds of encryption and decryption operations.
Principle of Feistel network
A round function is used in the Feistel network. This function receives two input parameters, namely the packet data (half of the original data) and the subkey, and then generates data of the same length as the packet data.
Then use the data generated in the previous round and the other half of the original data to perform an XOR operation as the input of the next round of functions.
In this way, one round goes on and finally the encrypted data is generated.
The decryption process is similar to the encryption process, except that the encryption operation is reversed.
The number of rounds of the Feistel network can be increased arbitrarily. No matter how many rounds, it can be decrypted normally.
Decryption has nothing to do with round function f, and round function f does not need to have an inverse function. The round function can be designed to be sufficiently replicated.
Encryption and decryption can be implemented using exactly the same structure. From what we have mentioned above, we can see that there is actually no difference between encryption and decryption.
Feistel network example
We use a diagram to introduce Feistel's workflow:
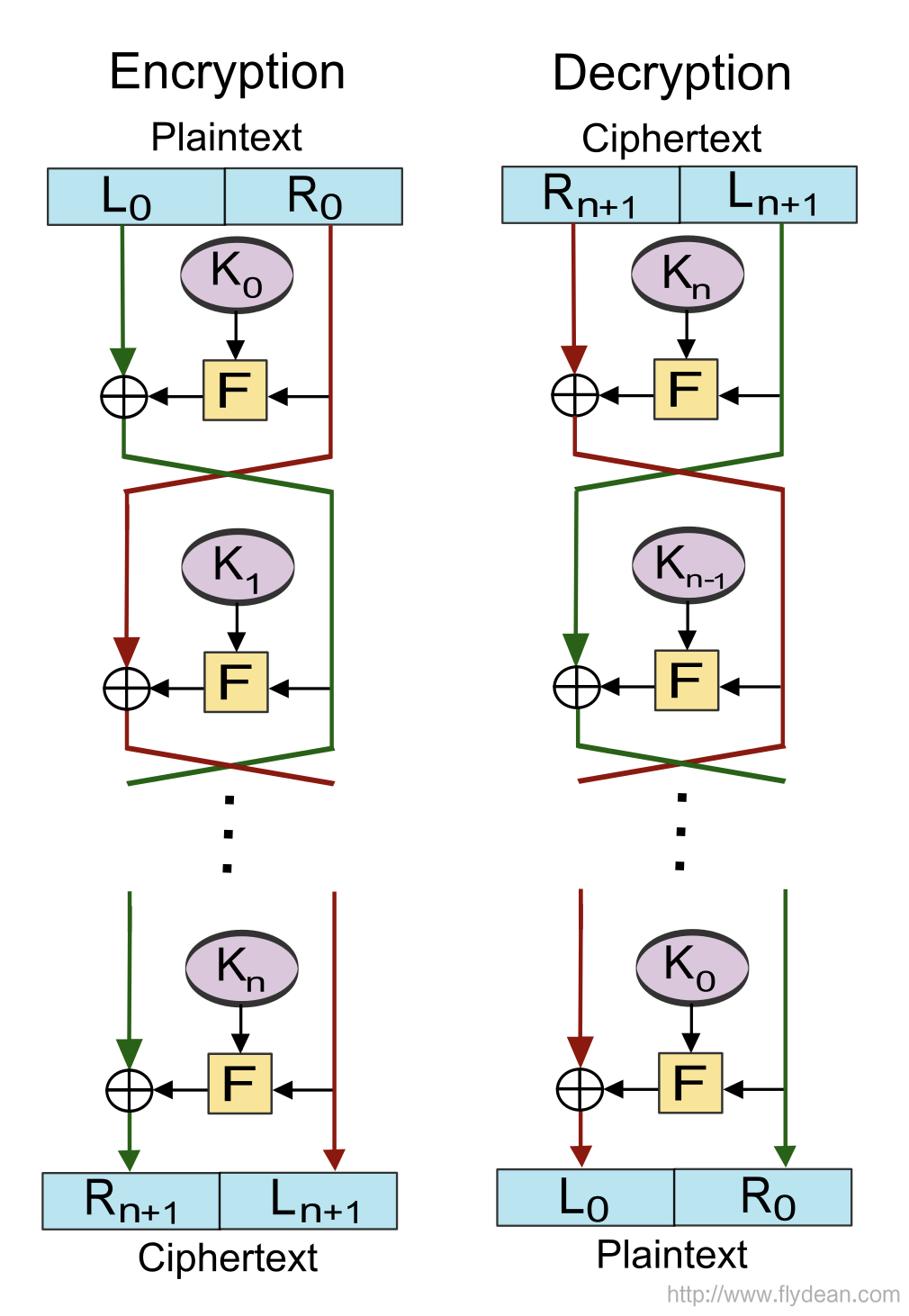
In the above figure, F represents the round function, which is also the round function.
K 0 , K 1 , K 2 ..., K n represents the subkeys of each round, respectively.
The original data is divided into equal parts on the left and right sides, (L 0 , R 0 )
Each round will perform the following operations:
- Li+1 = Ri
- Ri+1 = Li XOR F(Ri,Ki)
The final encryption result is (R i+1 , L i+1 )
The decryption process is the reverse of the encryption process, and each round of decryption will perform the following operations:
- Ri = Li+1
- Li = Ri+1 XOR F(Li+1,Ki)
Finally we get our original data (R 0 , L 0 )
Theoretical Research on Feistel Network
Michael Luby and Charles Rackoff proved that if the round function is i as the seed, then after three rounds of operations, the generated block cipher is already pseudo-randomly arranged. After four rounds of operations, a "strong" pseudo-random arrangement can be generated.
What is a pseudo-random number?
Consider if a random number is generated in a computer, because the data in the computer is composed of 0 and 1, all the data are deterministic, either 0 or 1, so computer programs cannot generate real random numbers.
If you want a computer to generate random numbers, the usual way is to calculate the input through a certain algorithm function to get the processed number.
If the algorithm function is deterministic, that is to say, the same input can get the same output, then this number is not generated randomly, and this number is called a pseudo-random number.
Pseudo-random numbers are calculated by a deterministic algorithm from a sequence of uniformly distributed random numbers from [0,1]. It is not truly random, but has statistical characteristics similar to random numbers, such as uniformity and independence.
Because the research of Luby and Rackoff is very important, the Feistel cipher is also called Luby-Rackoff cipher.
Expansion of Feistel network
In addition to the DES we introduced before, many algorithms use the Feistel network structure, such as Blowfish, Twofish, and so on.
Because of the symmetrical nature and simple operation of the Feistel network, it is very simple to implement the Feistel network by hardware, so the application of the Feistel network is very extensive.
This article has been included in http://www.flydean.com/feistel-cipher/
The most popular interpretation, the most profound dry goods, the most concise tutorial, and many tips you don't know are waiting for you to discover!
Welcome to pay attention to my official account: "Program those things", know technology, know you better!
**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。