Introduction to introduces how the EMR high-security cluster uses Kerberos and Apache Ranger for authentication and access authorization management
Direct best practice: [ EMR cluster security authentication and authorization management ]
Best Practice Channel: [ Click to view more cloud best practices ]
There are a wealth of best practices for enterprise cloud migration. Starting from typical scenarios, we provide a series of project practice solutions to lower the threshold for enterprise cloud migration while meeting your needs!
Scene description
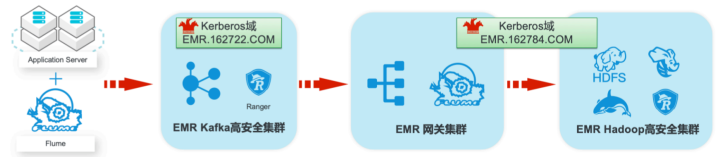
Alibaba Cloud EMR service Kafka and Hadoop security clusters use Kerberos for user security authentication, and Apache Ranger service for access authorization management. In this best practice, Apache web server logs are used as an example to demonstrate the construction of a log big data warehouse based on the ecological components of Kafka and Hadoop, and introduce how to configure authentication and authorization through Kerberos and Ranger in the entire data process.
Solve the problem
1. Create a Kerberos-based EMRKafka and Hadoop cluster.
2. Kerberos related configuration and usage methods in Kafka and Hadoop clusters of EMR service.
3. Add Kafka, HDFS, Hive and Hbase services and access strategies to Ranger.
4. Security configuration related to Kafka and HDFS in Flume.
Product List
- E-MapReduce
- VPC
- Cloud server ECS
- ApsaraDB for RDS
Copyright Statement: content of this article is contributed spontaneously by Alibaba Cloud real-name registered users. The copyright belongs to the original author. The Alibaba Cloud Developer Community does not own its copyright and does not assume corresponding legal responsibilities. For specific rules, please refer to the "Alibaba Cloud Developer Community User Service Agreement" and the "Alibaba Cloud Developer Community Intellectual Property Protection Guidelines". If you find suspected plagiarism in this community, fill in the infringement complaint form to report it. Once verified, the community will immediately delete the suspected infringing content.

**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。