Foreword:
Hello everyone, today I will introduce to you some common security problems in the web security field.
1. SQL injection
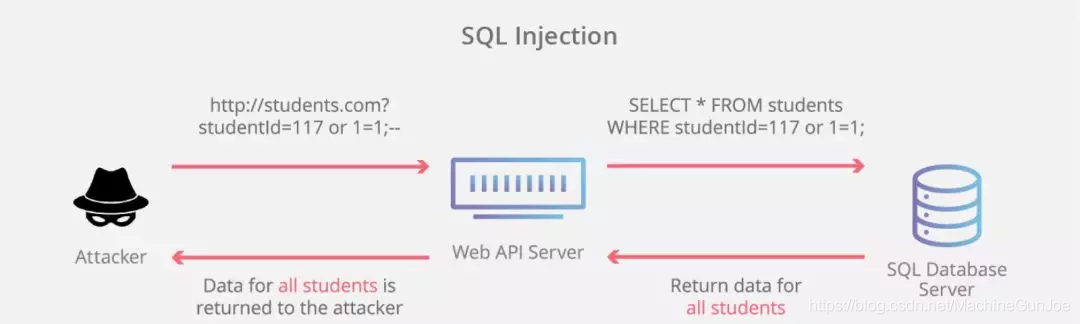
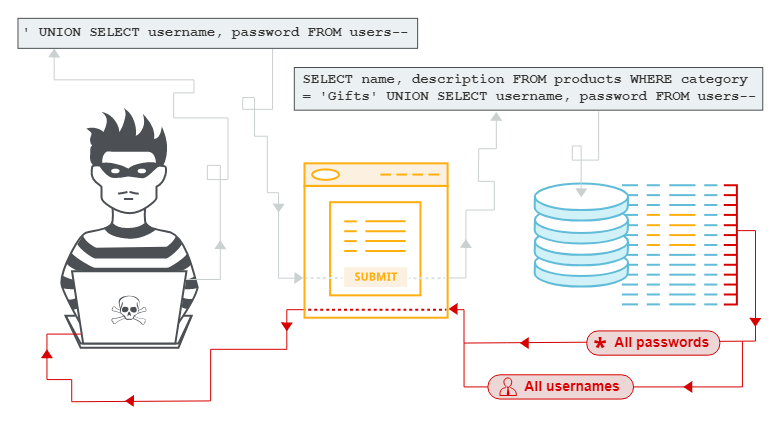
The core of the SQL injection attack is to allow the Web server to execute the SQL statement expected by the attacker in order to obtain the data of interest in the database or perform operations such as reading, modifying, deleting, and inserting the database to achieve its evil purpose.
And how to make the Web server execute the attacker's SQL statement? The conventional method of SQL injection is to place SQL statements in the form or request parameters and submit them to the back-end server. If the back-end server does not check the input security, it will directly take out the variables for database query, which is very easy to be tricked.
as follows:
For an interface that obtains user information based on user ID, the back-end SQL statement generally looks like this:
select name,[...] from t_user whereid=$idAmong them, $id is the user id submitted by the front-end, and if the front-end request is like this:
GET xx/userinfo?id=1%20or%201=1After the request parameter id is escaped, it is 1 or 1=1. If the backend does not perform security filtering and directly submits the database query, the SQL statement becomes:
select name,[...] from t_user whereid=1or1=1The result is to find out all the data in the user table, achieving the hacker's purpose of leaking data.
The above is just a very simple example. In a real SQL injection attack, the parameter structure and SQL statement are much more complicated than this, but the principle is the same.
2. XSS attack
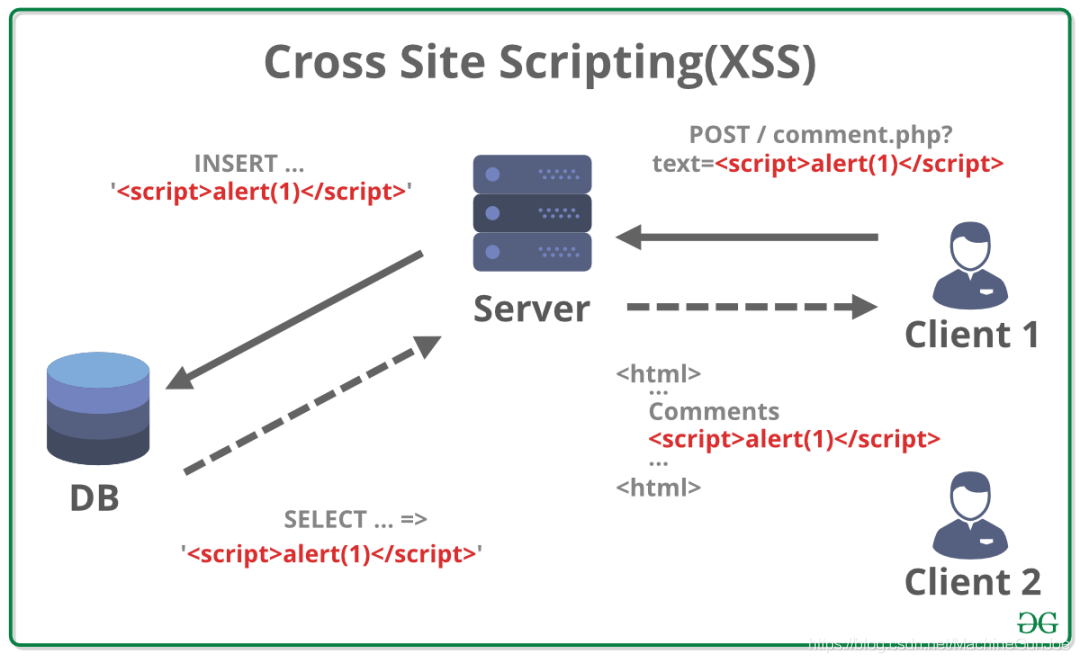
XSS stands for Cross Site Scripting (Cross Site Scripting). In order to distinguish it from overlapping style sheets CSS, another abbreviation XSS is changed.
The core of an XSS attack is to embed executable front-end script code (usually JavaScript) into a web page. It sounds awkward. In the vernacular, the attacker wants your browser to execute the JS code he wrote. How can it be done? Generally XSS is divided into two types:
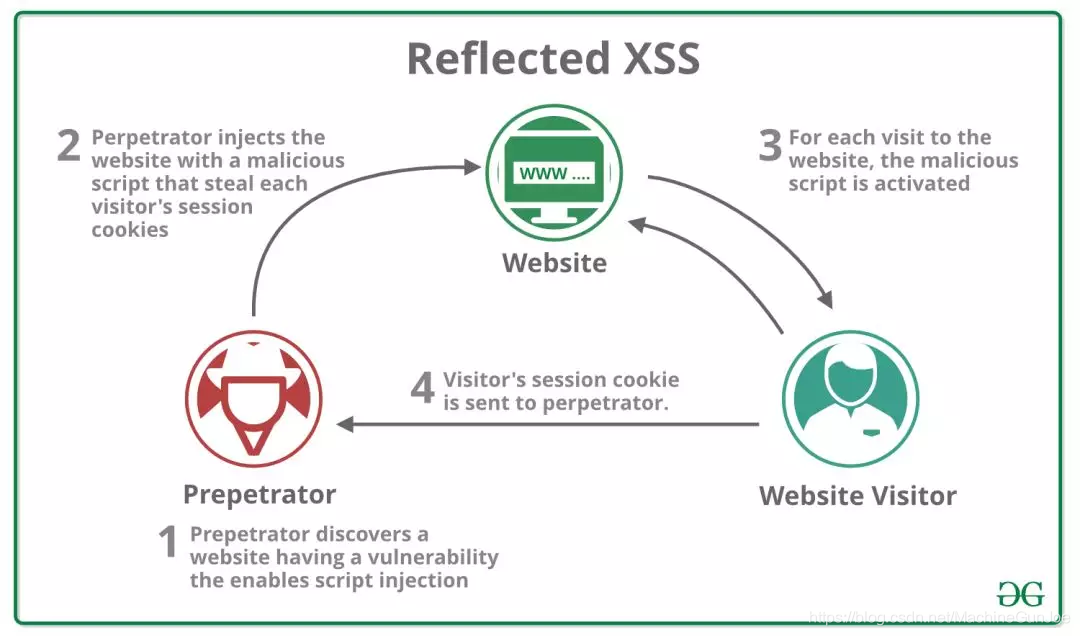
reflective type
1. The attacker puts the JS code as a request parameter in the URL to induce the user to click
Example:
http://localhost:8080/test?name=<script>alert("you are under attack!")</script>2. After the user clicks, the JS is passed to the back end of the web server as a request parameter
3. The back-end server does not check and filter, and after simple processing, put it into the body of the webpage and return it to the browser
4. The browser parses the returned webpage and wins!
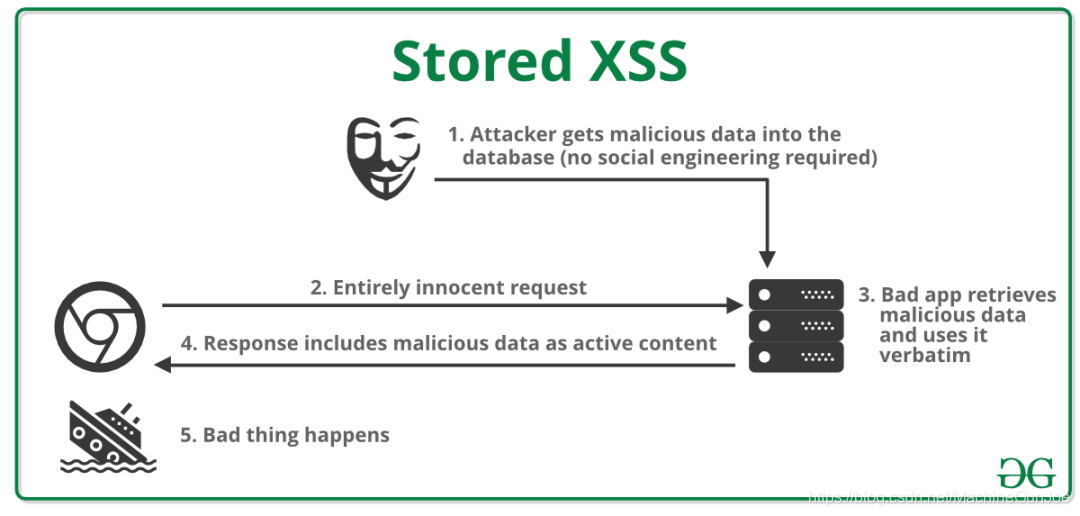
storage type
The attack script in the above method is directly transferred to the server and then returned to the browser to trigger execution. The difference between the storage type and the attack script is that the attack script can be stored in the database, and then the attack script is rendered into the web page when querying later, and then returned to the browser to trigger execution. . Examples of common routines are as follows:
1. The attacker's webpage replies, the post contains JS script
2. After the replies are submitted to the server, they are stored in the database
3. Other netizens view the post, query the reply content of the post in the background, build a complete web page, and return to the browser
4. The netizen's browser renders the returned webpage, and he wins!
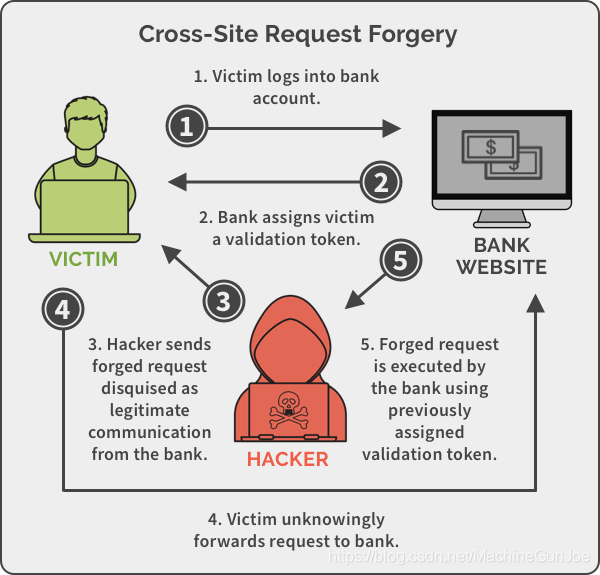
3. CSRF attack
CSRF, cross-site request forgery, its core idea is to open another Tab page to open malicious website B when opening website A. At this time, under the "instigation" of page B, the browser initiates an HTTP request to website A . The harm of this process lies in 2 points:
1. This HTTP request is not the user's active intention, but "instigated" by B. If it is a more harmful request operation (email? Delete data? etc.), it will be troublesome.
2. Because website A has been opened before, and the browser has cookies issued by A or other information used for identity authentication, this time the "instigated" request will automatically bring this information, and the backend of website A will be divided into It’s not clear whether this is the real intention of the user
4. DDoS attacks
DDoS stands for Distributed Denial of Service: Distributed Denial of Service attack. It is an upgraded version of a denial of service attack. The denial of attack service, as the name implies, makes the service unavailable. It is often used to attack servers that provide external services, like common ones:
Web service
Mail service
DNS service
Instant messaging service
......
Attackers keep making service requests, so that legitimate users' requests cannot be processed in time. This is a DoS attack.
An attacker uses multiple computers or computer clusters to conduct a DoS attack, which is a DDoS attack.
In the early days when the Internet technology was not so developed, it was easy to launch a DoS attack: a computer with strong performance, write a program and multi-threaded to continuously make requests to the server, the server is overwhelmed, and ultimately cannot handle normal requests. To other normal users, it looks like the website is inaccessible, and denial of service is what it means.
Later, with the development of technology, the current server is no longer as simple as a server. When you visit a domain name of www.baidu.com, there are countless CDN nodes and countless Web servers behind it.
In this case, I still want to rely on a single computer to try to make a network service fully loaded, which is no different from an egg hitting a stone.
Technology has always been a double-edged sword. Distributed technology can be used to provide highly available services and can also be used by attackers to carry out mass destruction attacks. The attacker is no longer limited to the attack capability of a single computer, but instead launches a denial of service attack through a large-scale network cluster.
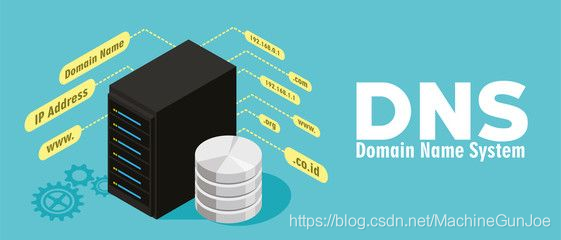
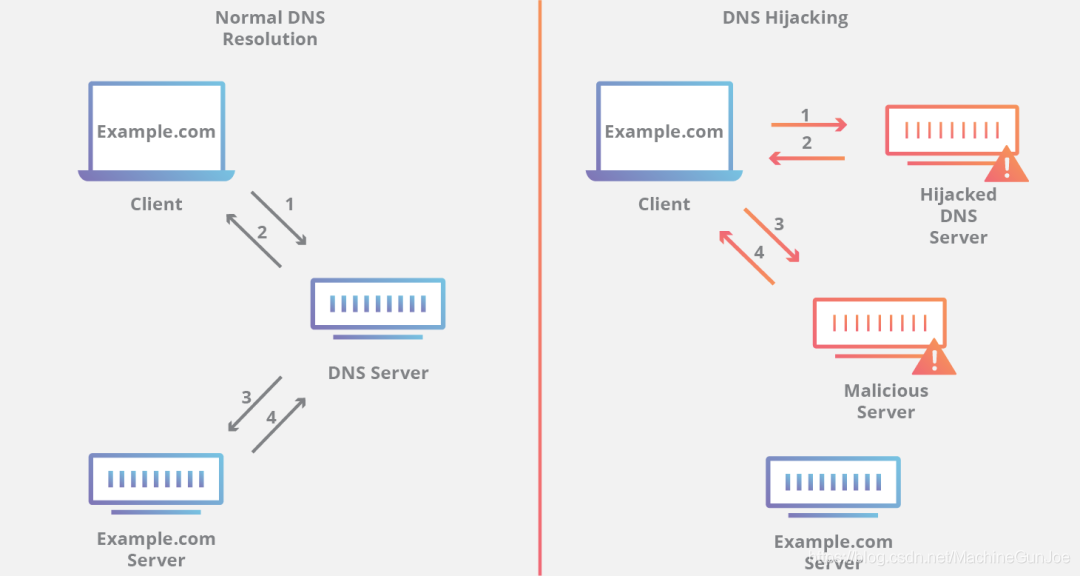
5. DNS hijacking
In today's Internet traffic, the traffic generated by Web services based on HTTP/HTTPS occupies the vast majority. The development of web services is in full swing, and behind this is inseparable from an obscure hero is the domain name resolution system:
If there is no DNS, we need to remember the IP address of each website instead of their domain name when surfing the Internet. This is a disaster. Fortunately, DNS does all this silently behind the scenes. We only need to remember one domain name and leave the rest to DNS. Come and finish.
It is precisely because of its importance that people with ulterior motives will naturally not let it go, and DNS hijacking technology was invented.
DNS provides services to convert domain names into IP addresses. However, in the design of the early protocol, the security was not considered too much. For the querying party:
Is it really a DNS server that I am requesting? Is it someone impersonating?
Has the query result been tampered with? Does this IP really belong to this website?
There is no mechanism in the DNS protocol to guarantee that these questions can be answered, so DNS hijacking is very widespread. From the moment a user enters a domain name in the address bar, dangers along the way are hard to guard against:
The Trojan in the local computer modifies the hosts file
The Trojan in the local computer modifies the response in the DNS packet
Nodes in the network (such as routers) modify the response in the DNS packet
Nodes in the network (such as operators) modify the response in the DNS packet
......
Later, in order to verify the received DNS response on the client side, DNSSEC technology appeared, which can solve some of the above problems to a certain extent. However, due to some reasons, this technology has not been used on a large scale, especially in China, where there are few deployment applications.
Later, leading Internet vendors such as Alibaba and Tencent began to launch httpDNS services, and they came to a trick to draw salaries. Although the name of this technology still has the three letters of DNS, the implementation is as good as the original, but DNS is already a world of difference. No, through this technology, DNS has become an application service on top of the http protocol.
6. JSON hijacking
JSON is a lightweight data exchange format, and hijacking is to steal data (or it should be called hijacking, interception is more appropriate. Malicious attackers use some specific means to perform JSON data that should be returned to the user. Intercept and send the data back to the malicious attacker. This is the general meaning of JSON hijacking. Generally speaking, the JSON data hijacked contains sensitive information or valuable data.
7. Brute force cracking
This is generally for passwords. Weak passwords are easily guessed by others (people who know you well, etc.) or brute force cracked by cracking tools.
The password complexity of the solution must be large enough, and it must be concealed enough to limit the number of attempts
8. HTTP header tracking vulnerability
The HTTP/1.1 (RFC2616) specification defines the HTTP TRACE method, which is mainly used by the client to test or obtain diagnostic information by submitting a TRACE request to the Web server.
When TRACE is enabled on the Web server, the submitted request header will be returned in the body of the server response. The HTTP header is likely to include Session Token, Cookies or other authentication information. Attackers can use this vulnerability to deceive legitimate users and obtain their private information.
solution:
Disable the HTTP TRACE method.
9. Information Leakage
Because the web server or application program does not correctly handle some special requests, some sensitive information of the web server is leaked, such as user name, password, source code, server information, configuration information, etc.
So generally pay attention to:
When the application reports an error, no external debugging information is generated. The data and special characters submitted by the user are filtered to ensure the security of the source code and server configuration.
10. Directory Traversal Vulnerability
The attacker sends a request to the Web server, by appending ../ in the URL or in a directory with special meaning, or appending some variants of ../ (such as ..\ or ..// or even its encoding), resulting in an attack Users can access unauthorized directories and execute commands outside the root directory of the Web server.
11. Command execution vulnerability
Command execution vulnerability is to initiate a request through a URL, execute unauthorized commands on the Web server, obtain system information, tamper with system configuration, control the entire system, and paralyze the system.
12. File upload vulnerability
If the file upload path variable is not strictly filtered, and the file suffix and file type uploaded by the user are not strictly restricted, the attacker can upload any file through the web-accessed directory, including the website backdoor file (webshell), and then remotely control the website server.
So generally pay attention to:
In the process of developing websites and applications, it is necessary to strictly restrict and verify the uploaded files, prohibit uploading malicious code files, limit the execution permissions of related directories, and prevent webshell attacks
13. Other vulnerabilities
- SSLStrip attack
- OpenSSL Heartbleed security vulnerability
- CCS injection vulnerability
- Certificate validity verification vulnerability
14. Business Vulnerabilities
General business vulnerabilities are related to specific applications, such as parameter tampering (serial number ID/order, 1 yuan payment), replay attack (disguised payment), permission control (unauthorized operation), etc.


**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。