Hello everyone, I am a side dish.
A man who hopes to be about architecture ! If you also want to be the person I want to be, otherwise click on your attention and be a companion, so that Xiaocai is no longer alone!
This article mainly introduces common web attack methods in the
If necessary, you can refer to
If it helps, don’t forget 16118ecbaaa9a0 ❥
The WeChat public account has been opened, , students who have not followed please remember to pay attention!
During lunch, reader Xiao Li chatted with me about the interview process last week. The classic high and low. The answer at the beginning of the interview was okay, but it was not satisfactory at the end. One of the interview questions caught my attention. The interviewer asked Xiao Li: Do you know what kinds of common Web attack methods are?
Web attack methods? For the development programmer, it should come casually, but Xiao Li only answered the SQL injection attack . After asking Xiao Li, learned that the 16118ecbaaa9fd Web attack method generally seen on the usual blog, but there is almost no protection in the development, because most of the products he is responsible for are TB , so the attack methods are usually I knew it when I saw it, but I almost forgot it when I saw it. Seeing the friends here, after thinking about it, I can say several Web attack methods, and how to protect them? If it's a bit vague, let's review the common Web attack methods in this article~!
Web attack
In the Internet, there are countless attack methods. We can't usually use ourselves as ordinary development programmers rather than security-oriented developers as a reason, instead of mastering the basic Web attack methods! Let’s get acquainted with the common Web attack methods
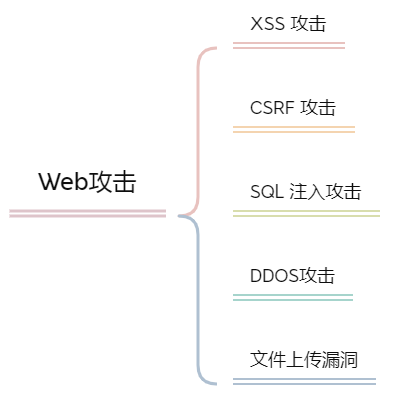
Common Web attack methods mainly include XSS attack, CSRF attack, SQL injection attack, DDos attack, file vulnerability attack and so on. The protection methods of these attack methods are not complicated, but many companies have suffered from this attack.
1. XSS attack
The full name of the XSS Cross Site Scripting (Cross Site Scripting)
Why is it not called CSS , because it is not confused with Cascading Style Sheet (CSS)XSS attack is of the most common attack methods in the 16118ecbaaab17 Web
Cross-site scripting attack , keyword script.
Attackers often embed malicious scripts in web pages. When the user opens the web page, the scripts begin to execute in the background of the client’s browser. They are often used to steal the client’s cookie , username and password, and download and execute viruses. Trojan horse program, and obtain the client Admin permissions.
1. Attack principle
Submit information to the background in the form of common front-end forms
<input type="text" name="username" value="cbuc" />A very common piece of html code, submit username information to the background, under normal circumstances, users will usually enter their own username , there is no problem at this time, but under abnormal circumstances, the user input is not A normal string, but "/><script> alert("bingo") </script><!- . Press this time the content of the form will become
<input type="text" name="username" value=""/><script> alert("bingo") </script><!-" />At this time, the parameters are submitted to the background. Due to the illegality of the username, the verification may not pass, and the server will redirect to the page with the above parameters. At this time, a warning box will pop up on the page:
The warning box is not a big problem, because it depends on this script. If the attacker makes a slight modification, the nature may be different~
Furthermore, the attacker can operate on the URL, and the address normally submitted is
www.xxx.com/login?username="/><script> alert("bingo") </script><!-"The attacker can encode the URL to confuse the user:
www.xxx.com/login?username="%2F%3E%3Cscript%3E%20alert(%22bingo%22)%20%3C%2Fscript%3E%3C!-"2. Protection methods
Knowing how to attack, it is not difficult to defend, and we can prescribe the right medicine. Since the input parameters are illegal, it is necessary for us to verify the input parameters, such as <、>、"、"、'、' , we need to escape and verify.
2. CSRF attack
CSRF attack full name Cross site request forgery (Cross site request forgery). It is a malicious use of a website. The 16118ecbaaad7b XSS attack by using trusted users in the site to trigger scripts by themselves. The CSRF uses the attacked website by disguising requests from trusted users.
CSRF attack , keywords: forgery.
This attack steals the identity of the visiting user and sends malicious requests to third-party websites in the name of the visitor. It is often used to use the identity of the visitor to send messages, conduct transaction transfers, and steal account numbers.
1. Attack principle
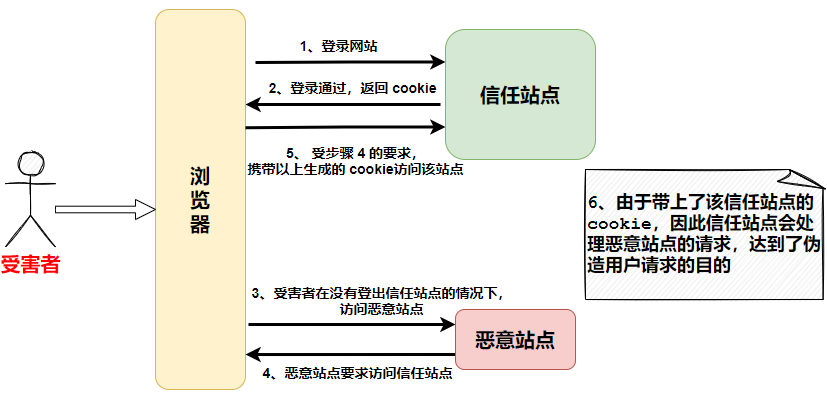
victim first completes the login on the trusted site , and generates a cookie, which will be stored in the browser for a certain period of time. At this point, if the user visits the malicious site trusted site , at this time the malicious site will initiate the above request to the trusted site , and this request will bring the above request to the 16118ecbaaae7a trusted site 16118ecbaaae7c. Cookie, when a malicious request comes to the trusted site , and the trusted site sees the cookie carried in the request, it will determine that the request is sent by the victim Therefore trusted sites will be based victims to complete the rights malicious requests of command, and this command may be use victims identity to send messages, transfer payments, etc. operations, such malicious site on the purpose of forging victim request trust site 16118ecbaaae99.
Seeing this process, I don’t know if you are enlightened, or if the QQ front of the screen have experienced the embezzlement of 06118ecbaaaeb8. Of course, some embezzlement methods are similar to the above process.
This attack method is very common in daily life. If the transfer address of a certain payment system is www.xxx.com/pay?accountNum=xxxx&money=xxx . Among them, accountNum is the account for transfer purpose, money is the transfer amount. At this time, if you happened to log in to the payment system, but did not log out in malicious site, if you click on a picture, the address of the picture is:
<img src="www.xxx.com/pay?accountNum=xxxx&money=xxx" />When you browse the pictures happily, you don't know that your account has been quietly missing the specified amount at this time!
This is because you did not log out of the payment system in time, and clicked on the malicious link malicious site, carrying your unexpired cookies, and successfully stealing your money.
2. Protection methods
Also know the disease and get the right medicine! The protection measures are as follows:
1) Set the cookie to HttpOnly
CSRF key attacks is that the user does not use the expired cookies , then in order to prevent cookies steal, it is necessary in cookies arrangement the HttpOnly properties, so that by a program ( XSS attacks) to Cookie information cannot be read, which prevents attackers from forging Cookie .
2) Increase token
This protection method is also aimed at Cookie , because all user authentication information in the request is stored in Cookie , because the key to CSRF put the attacker in the request? Forged information , and the information cannot be stored in Cookie . Then we can add a randomly generated token token when the request comes. If the check fails, it is considered to be a CSRF attack and the request is rejected.
3) Through Referer
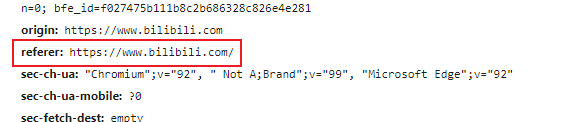
According to the HTTP protocol, there is a field HTTP referer , which records the source address Http Under normal circumstances, all requests to access a security-restricted page come from the same website.
The malicious request in the CSRF is sent from the malicious site , so to defend against the CSRF attack, you need to verify the referer value for each request.
Three, SQL injection attacks
SQL injection is the most frequently encountered by programmers. The so-called SQL injection is achieved by SQL command as a normal request parameter and passing it to the server to trick the server into finally executing the malicious SQL command . The purpose of the invasion. Attackers often use the SQL injection vulnerabilities to query unauthorized key information, modify the data of the database server, and change the table structure, which is extremely harmful!
1. Attack principle
We often query whether the user exists or not through the following SQL:
SELECT * FROM s_user WHERE username = '' and password = '' When our backend uses the following code to query, there will be a fatal vulnerability
Connection con = getConnection();
Statement st = (Statement) con.createStatement();
String sql = "SELECT * FROM s_user WHERE username = '"+ username +"' and password = '"+ passward+"' ";
ResultSet rs = st.executeQuery(sql);
while(rs.next()){
...
}The above code logic is the use of front-end database query parameters passed, no problem feeling at first glance, but this time if password front end pass over the value of ' or '1'='1
Then SQL will become
SELECT * FROM s_user WHERE username = '' and password = '' or '1'='1' This kind of SQL will find out all the users in the database without trying, and it will return the login success without entering the correct password. And this is a simple and typical SQL injection attack.
' or '1'='1 harm of 06118ecbaab234 is to allow users to log in without a password. If the value passed is '; drop table xxx; -- the problem will be serious at this time!
2. Protection methods
1) Use prepared statements
Prepared statement is an interface in java.sql, inherited from Statement interface.
The difference between the statement and 16118ecbaab28b Statement is that the SQL statement is specified when the PreparedStatement DBMS for compilation. When the compiled statement needs to be executed, DBMS The compiled SQL statement, without the need to compile it first like other SQL statements:
String sql = "SELECT * FROM s_user WHERE username = ? and password = ? ";
PreparedStatement st = conn.preparedStatement(sql);
st.setString(1, username);
st.setString(2, password);
ResultSet rs = st.executeQUery();As you can see, the original white energy in the SQL statement has been used as a placeholder? Instead, the variables are set setString()
2) Use ORM framework
The key method to prevent SQL injection is to escape some keywords, and some common ORM frameworks, such as Mybatis, Hibernate, etc., all support the escape of keywords or special symbols in response, which can be easily configured. It prevents SQL injection vulnerabilities and lowers the threshold for ordinary developers to perform secure programming.
Fourth, file upload vulnerabilities
Many websites have upload functions, such as uploading pictures, files, compressed packages, and so on. These resources are often stored on remote servers. A file upload attack refers to an attacker using some sites that did not properly verify the file type, uploading executable files or scripts, and performing certain permission operations on the server through the scripts, or by inducing external users to access the files. Script file to achieve the purpose of the attack.
Of course, this kind of attack protection is relatively simple. In order to prevent users from uploading malicious executable script files and use the file upload server as a free file storage server, we need to whitelist the type of uploaded file, and The size of the uploaded file needs to be limited, and the uploaded file needs to be renamed, so that the attacker cannot guess the access path of the uploaded file.
Among them, the whitelist verification of the type of the uploaded file cannot judge the type of the file by the suffix name alone, because the attacker may be able to upload the file by changing the suffix name of the executable file to another uploadable suffix name. Because judging the file type requires a more secure way.
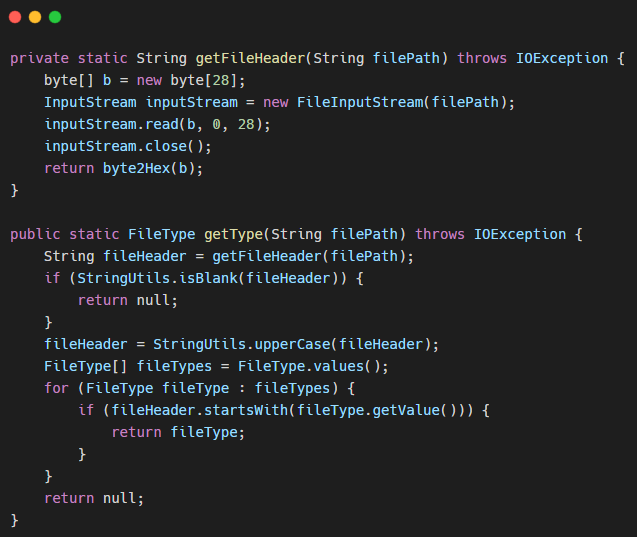
For many types of files, the content of a few bytes is actually fixed, so based on the content of these bytes, the file type can be determined, and these bytes are also magic number 16118ecbaab380
The above is the magic number of the file type, and then we judge the file type by comparing the file header of the file with the magic number of the file type
Five, DDOS attack
DDos attack also known as distributed denial of service attack (Distributed Denial of Service), is currently one of the most powerful and difficult to defend against.
Before understanding DDoS , we need to know what DoS . The most basic DoS is to use a reasonable client request to occupy too much server resources, so that legitimate users cannot get a response from the server. DDoS attack is a type of attack based on the DoS The traditional DoS attack is generally a one-to-one method. When the target’s CPU speed, memory, or network bandwidth and other performance indicators are not high, its effect is obvious, but with computer and network technology With the development of the computer, the processing power of the computer has increased significantly, and the memory has continued to increase, which makes the DoS attack gradually lose its effect.
This is the same as the evolution of a single application to a distributed architecture. The traditional DoS evolved to distributed DoS (DDoS) .
1. Attack principle
DDoS attack refers to an attacker who uses a public network to combine a large number of computer equipment as an attack platform to launch an attack on one or more targets, so as to achieve the purpose of paralyzing the target host. Usually before the attack starts, the attacker will control a large number of user computers in advance. This type of computer is called broiler, and through instructions, a large number of broilers can access a certain host at the same time, so as to achieve the purpose of paralyzing the target host. .
2. DDoS classification
DDoS is an attack method, which is divided into several types DDoS attacks
1)SYN Flood
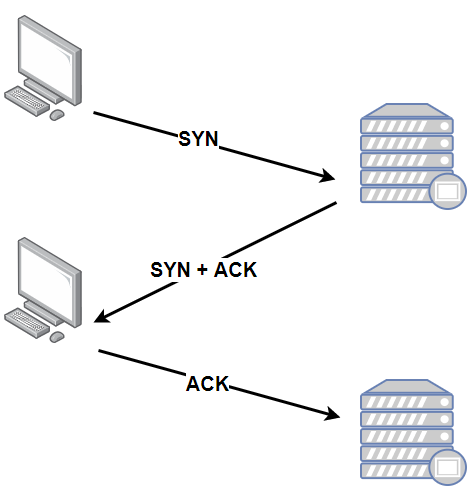
SYN Flood is one of the most classic attack methods on the Internet. To understand this attack method, we need to start with the process of TCP As we all know, TCP protocol must establish a connection based on TCP protocol before communication, the following is the process of establishing a connection:
This is a very recommended TCP three-way handshake process.
- In the first step, the client sends a SYN . SYN means Synchronized. The SYN message will indicate the port number of the client and the initial serial number of the TCP connection.
- In the second step, after the server receives the SYN message from the client, it will return a SYN+ACK message, indicating that the client request is received, and the TCP sequence number is increased by 1, ACK is confirmation ( Acknowledgment) mean
- In the third step, after the client receives the SYN + ACK message from the server, it will also return a ACK report to the server. Similarly, the TCP sequence number is increased by 1, and then the TCP connection is established. , And then data communication can be carried out.
TCP protocol is a reliable transmission protocol. Some exception handling mechanisms are set up during the three-way handshake. In the third step, if the server does not receive the ACK message from the client, the server will generally retry, that is, send the SYN + ACK message to the client again, and it has been in the state SYN_RECV The client joins the waiting list; on the other hand, after the server sends a SYN + ACK message, it will pre-allocate some resources to the upcoming TCP connection. This resource has been reserved while waiting for retry, due to the server's resources Limited, after the waiting list that can be maintained exceeds the limit, no new SYN messages will be received, which means that a new TCP connection is refused.
At this time, we can talk about the SYN Flood is going on, SYN Flood is to use the TCP protocol three-way handshake process to achieve the purpose of the attack. The attacker forged a large number of IP addresses to send a SYN message to the server. Because the forged IP address cannot exist and it is impossible to get any response from the client, it will always be stuck at third step , and the server will It is necessary to maintain a very large semi-connection waiting list, and constantly traverse and retry the IP addresses in this list, which consumes a lot of system resources. However, due to limited server resources, malicious connections fill up the server's waiting queue, causing the server to no longer receive new SYN requests, making normal users unable to complete communication.
2)DNS Query Flood
DNS Query Flood actually a UDP Flood attack, because the DNS service has an irreplaceable role in the Internet, so once the DNS server down, the impact will be very large!
DNS Query Flood attack is to send massive domain name resolution requests to the attacked server. This part of the domain names requested for resolution are generally randomly generated, most of which do not exist, and forged ports and client IPs are used to prevent query requests from being by 16118ecbaab796 ACL (Access Control List). After the attacked DNS server receives the request for domain name resolution, it will first check whether the domain name’s IP is on its own server. Because the domain name does not exist, it can’t be found by itself, so DNS server It will recursively query the domain name from the upper DNS server until the 13 root DNS servers of the global Internet. A large number of non-existent domain name resolution requests bring a lot of load to the server. When the resolution request exceeds a certain level, it will cause the DNS server resolve the domain name timeout, making normal domain names unable to query the corresponding IP. Achieved the effect of an attack.
3) CC attack
CC (Challenge Collapsar) attack is an attack based on the application layer HTTP protocol, also known as HTTP Flood
CC attack on is to control a large number of "broiler" or use a large number of anonymous HTTP proxies searched from the Internet to simulate normal users to initiate requests to the website until the website refuses service. Most websites will use CDN and distributed caching to speed up server response and improve website throughput. These malicious HTTP requests deliberately avoid these caches, requiring multiple DB query operations or one request will return a large amount of data, accelerating the consumption of system resources, and thus dragging down the back-end business processing system.
The above are the common web attack methods, knowing the reason, knowing the reason, security is extremely important and extremely difficult to defend, every developer should pay attention to it!
Don't talk about it, don't be lazy, and be a X as an architecture with Xiaocai~ Follow me to be a companion, so that Xiaocai is no longer alone. See you below!
If you work harder today, you will be able to say less begging words tomorrow!
I am Xiaocai, a man who becomes stronger with you.
💋The WeChat public account has been opened, , students who have not followed please remember to pay attention!



**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。