AES
AES, Advanced Encryption Standard, is a standard that uses block encryption, also known as Rijndael encryption. Strictly speaking, AES and Rijndael are not exactly the same. The block length of AES is fixed at 128 bits, and the key length can be 128 , 192 or 256. The Rijndael encryption method can support a larger range of block and key lengths. The key and block length used by Rijndael can be 128, 192 or 256 bits. AES is one of the most popular algorithms for symmetric encryption .
We will not discuss the specific implementation of AES, because a large amount of advanced mathematics knowledge is used in it. It is actually meaningless to simply understand the AES process (it is difficult to understand without a mathematical foundation), so today we will focus on summarizing some small aspects in the use process. point.
Encryption mode-ECB, CBC
Of course, the encryption modes of block ciphers are not only ECB and CBC, and we will not cover the others for the time being.
The AES mentioned above is a standard for block encryption.The encryption mode can actually be understood as the way and connection of processing different blocks.
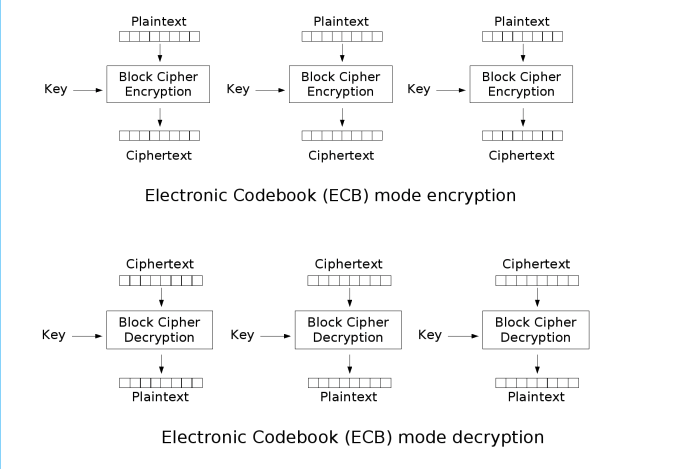
ECB
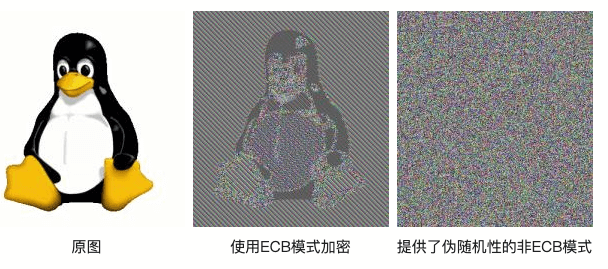
ECB can be regarded as the simplest model. The data that needs to be encrypted is divided into N blocks according to the size of the block, and each block is encrypted independently
The disadvantage of this method is that the same plaintext block will be encrypted into the same ciphertext block. Therefore, in some cases, this method cannot provide strict data confidentiality. It is easy to understand through the following example
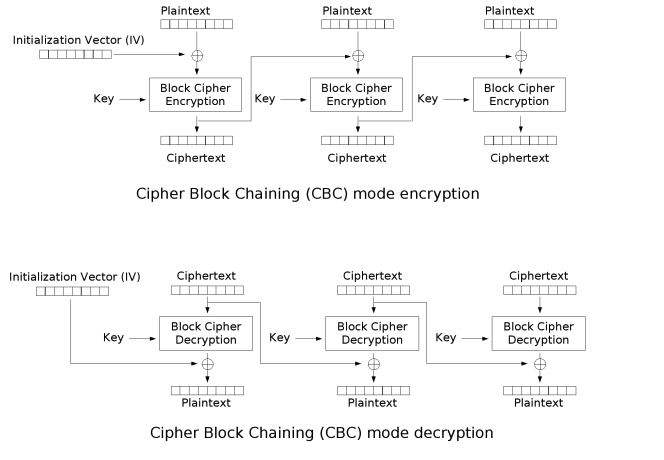
CBC
This mode is used in our project. In CBC mode, after each plaintext block is XORed with the encryption result of the previous block, it is encrypted, so the encryption of each block depends on the encryption result of the previous block. At the same time, in order to ensure the encryption of the first block, an initialization vector iv needs to be introduced in the first block.
CBC is the most commonly used mode. Its disadvantage is that the encryption process can only be serial and cannot be parallel, because the encryption of each block depends on the encryption result of the previous block. At the same time, there are slight changes in the plaintext during encryption. It will cause all subsequent ciphertext blocks to change. But this mode also has advantages. In the decryption process, the decryption of each block depends on the encryption result of the previous block, so when we want to decrypt a block, only It is necessary to read the previous block together to complete the decryption of this block, so this process can be operated in parallel.
Fill mode
The blockSize of each block of AES encryption is 128 bits, so if the data we want to encrypt is not a multiple of 128 bits, there will be the last block less than 128 bits, then how to deal with this block, use the padding mode. The following are commonly used Fill mode.
PKCS7 / PKCS5
The block size that PKCS7 can be used for padding is 1-255 bits, and the padding method is also easy to understand. Use the ASCII code paddingChar = chr(paddingSize) represented by the value paddingSize of the padding length to perform redundant padding on the data. (explained later)
PKCS5 can only be used to fill 8-byte blocks
Let's take AES(128) as an example. The data block length is 128 bits and 16 bytes. When PKCS7 padding is used, the padding length is 1-16. Note that when the encryption length is an integer multiple of 16, the padding length is the largest. 16 bytes should be filled. The reason is that when unpacking "PKCS7", the numerical length represented by the last byte will be taken as the data padding length according to the protocol. If the actual data length is exactly an integer multiple of 16, it will be unpacked. The real data will be lost when it is packaged.
Give an example where the blockSize is 8 bytes
| DD DD DD DD DD DD DD DD | DD DD DD DD 04 04 04 04 |There are less than 8 bytes in the second block, which is 4 bytes short, so fill it with 4 4s
Strictly speaking, PKCS5 cannot be used for AES, because AES is at least 128 bits (16 bytes). Only when using DES, which is a 64-bit blockSize algorithm, consider using PKCS5.
Combine project practice
Our project first used CryptoSwift for the encryption and decryption library, but later found that there were performance problems, so we changed to IDZSwiftCommonCrypto.
Here we combine the bottom of the project and the decryption to mention a point. For details, please refer to the summary written before. Because the player supports dragging, we are dragging to a point and going to the network to pull the corresponding When data, the range should be corrected. Generally, we will use the start and end of the range as a benchmark to find all the block ranges that contain this range. For example, the range we need is 10-20, which is what we should correct The range is 0-31, because the starting point 10 is in 0-15, and 20 is in 16-31. This is a regular range correction. (The first step is to find multiple points of 16).
But in practice, when we request a piece of data, it also involves the initialization of the decryptor. If we are requesting data from 0 to 31, because it starts from 0, our decryptor only needs to use the key and the initial iv. To initialize, if after the basic range correction in the first step, the data we request does not start from 0, then we need to continue to read 16 bytes of data, for example, after the first The revised range is 16-31, then we should read 16 bytes forward, which should be the 32 bytes of data 0-31. After getting the data, use the first 16 bytes (the previous block). Ciphertext) as iv to initialize the decryptor.
Another point to note is that in the process of data decryption, the next 16 bytes of data may be swallowed. I haven't looked at the source code for the time being, and I don’t know the specific reason. So to be on the safe side, our range is the best. It is to read 16 bytes backward.
refer to
Thanks for reading
Reference
https://zh.wikipedia.org/zh-cn/%E9%AB%98%E7%BA%A7%E5%8A%A0%E5%AF%86%E6%A0%87%E5%87%86
https://segmentfault.com/a/1190000019793040
https://ithelp.ithome.com.tw/articles/10250386

**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。