Preface
my country's communication technology iteration and digital economy development are entering a new stage. On January 12, the State Council issued the "14th Five-Year Plan for the Development of Digital Economy", proposing that by 2025, the digital economy will enter a period of comprehensive expansion, and the added value of the core industries of the digital economy will account for 10% of GDP. While pressing the accelerator button for the development of the digital economy, don't forget to fasten your "seat belt". In order to plug data security loopholes, it is crucial to establish a sound data security governance operation and maintenance system.
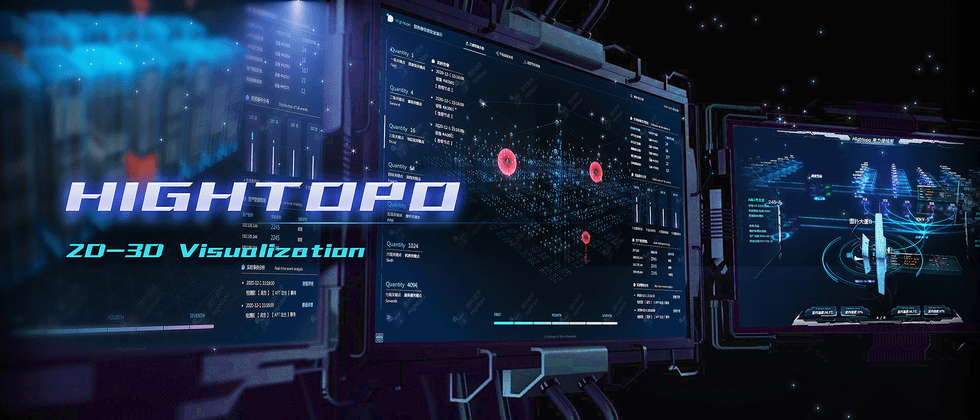
Tupu software uses the self-developed HT for Web product to create a server information security demonstration system, which realizes the digital and intelligent monitoring scene of the server. Online monitoring 1 national key point monitoring, 4 provincial key points, 16 urban key points, 64 venue key points, 256 building key points, 1024 computer room key points, and 4096 server key points. Through monitoring and early warning, detection and evaluation and other means, ensure the healthy and orderly operation of the server.
The setting of key points of level 1-7 can meet the needs of large-scale data center computer room. From the national computer room to the city computer room to individual equipment, there are nearly 6,000 bulletin boards, equipped with HT's unique bulletin board icons as display panels, which can adapt to various screens and different resolutions. Each bulletin board can carry different data information, which is more maneuverable.
Effect display
Hightopo uses lightweight 3D modeling technology to build three layouts of the server system, including 3D hierarchical relationship, plane hierarchical relationship, and underlying node hierarchy, to clearly present the nodes and connection relationships at different levels of the server.
System Analysis
Hightopo's rich visualization solution provides visualization and control over custom data center applications. It is similar to a network shooting range, simulating and reproducing the network architecture, system equipment, business process operating status and operating environment in the real cyberspace, so as to more effectively realize network security-related learning, research, inspection, etc. behaviors, thereby increasing the level of cybersecurity confrontation for personnel and institutions.
Defense Technical
With the wide application of network security protection equipment, the resulting network security alarms are also increasing day by day. How to efficiently alert network security, conduct accurate analysis and analysis, and discover potential network attacks is very important. Hightopo visually expresses the security defense technologies enabled in the physical space of the server through the digital space, realizing the whole process presentation and full cycle traceability, including APT attack defense, Trojan backdoor defense, virus attack defense, bot worm defense, etc., and accurate to specific devices , which provides the basis for regular maintenance and inspection of the running status of the network server.
HT also monitors high-risk APT attack events in real time, and supports managers to view and deal with them in a timely manner.
Service terminal damage event distribution
HT scans with the special killing tool of the backdoor program connected to the web page to check whether there is a virus source infection on the terminal, which leads to hackers taking control and launching network attacks on the server. Four service terminals A, B, C, and D are preset in the demonstration system to collect service monitoring results, and the number and number of events are displayed in a bar chart, which is convenient for business personnel to view key damaged terminals and grasp the law of harm. Through the statistical analysis of the risk vulnerability and virus scanning behavior of the attack terminal, it provides supporting materials for the preliminary judgment of subsequent events.
Asset Defense Strategy
With the help of information technology, it can monitor and track asset defense strategies, and improve the transparency of asset names, strategy names, and current status. The 2D panel visually displays the asset deployment situation, and the computer room administrator can rationally deploy the newly launched equipment according to the analysis results, so that the resource utilization of the computer room cabinet is more reasonable and sufficient. Continuously optimize the monitoring and operation management level, and continuously improve the service content and service level.
Live Warning
Real-time alarms are the most direct window for system maintenance personnel to find server faults. When the equipment fails, it can quickly locate the key points of the alarm and improve the speed of emergency management. The alarming device is highlighted and flashing in red, and the number of the faulty device is displayed on the 2D panel on the left.
Power System Wiring Diagram Visualization
The 2D and 3D power wiring configuration diagram drawn by HT technology can truly reflect the operation of the building power system, including accident lighting equipment, transformer location, line direction, etc. Real-time display of substation and building voltage, potential, real-time current power, to help maintain the stable operation of the power grid, reflecting the green and safe features of smart buildings and the flexible and interactive features of smart grids.
Combined with the real-time update of indoor temperature and humidity, it can help electrical workers to adjust indoor environmental parameters in changing climates such as high temperature and high humidity, and prevent equipment accidents caused by sudden changes in temperature.
Summary
While computer network services provide convenience, they also bring various security risks, including information leakage, system paralysis, etc., which not only threaten individual security, but also hinder the healthy development of computer network technology. In this regard, the server visualization monitoring system proposed by Hightopo enables it to prevent the emergence of various security risks while improving its own service capabilities, so as to create conditions for the safe operation of network servers.
For more industry application examples, please refer to the case link of Tupu Software's official website: https://www.hightopo.com/demos/index.html









**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。