foreword
The national secret is the domestic encryption algorithm recognized by the State Cryptography Administration. Protecting the security of important data through self-controllable domestic cryptographic algorithms is an important measure to effectively improve the level of information security. At present, my country's information systems in various important fields such as financial banking, education, transportation, communications, and defense industry have begun to upgrade and transform domestic cryptographic algorithms.
With the development of vehicle electrification, networking, and intelligence, vehicle operation safety, data security and network security risks are intertwined and superimposed. Provide support. In February 2022, the Ministry of Industry and Information Technology organized the compilation of the "Guidelines for the Construction of the Internet of Vehicles Network Security and Data Security Standard System" on the basis of the existing national vehicle networking industry standard system, of which GB/T 37376-2019 has been published. In the national standard documents such as "Format of Transportation Digital Certificate", the application and realization of national secrets are considered for all content related to cryptographic algorithms.
This article will introduce the classification and application of national secret algorithms in detail, and how to use EMQX to realize the integration of national secret certificates to ensure the security of Internet of Vehicles information.
Classification of State Secrets
In order to ensure the security of information transmission in financial, medical and other fields, the National Commercial Cryptography Administration has formulated a series of cryptographic standards, including SM1 (SCB2), SM2, SM3, SM4, SM7, SM9, Zu Chongzhi Cryptographic Algorithm (ZUC), etc. SM1, SM4, and SM7 are symmetric algorithms, SM2 and SM9 are asymmetric algorithms, and SM3 is a hash algorithm.
SM1 algorithm
The SM1 algorithm is a grouped symmetric algorithm, the group length is 128 bits, and the key length is 128 bits. The security and confidentiality strength of the algorithm and the performance of related software and hardware are comparable to AES. The algorithm is not public, and only exists in the chip in the form of an IP core. Using this algorithm, a series of chips, smart IC cards, smart password keys, encryption cards, encryption machines and other security products have been developed, which are widely used in e-government, e-commerce and various application fields of the national economy (including national government affairs, police affairs, etc.). important areas).
SM2 algorithm
The SM2 algorithm is an advanced and secure public key cryptographic algorithm, which is used to replace the RSA algorithm in our national commercial cryptography system. The SM2 algorithm is the ECC elliptic curve cryptographic mechanism, but it is different from international standards such as ECDSA and ECDH in terms of signature and key exchange, and adopts a more secure mechanism. In addition, SM2 recommends a 256-bit curve as the standard curve.
SM3 algorithm
SM3 is a hash algorithm whose essence is to add a fixed-length fingerprint to the data, which is 256 bits. It is used for digital signature and verification, message authentication code generation and verification, and random number generation in cryptographic applications, which can meet the security requirements of various cryptographic applications.
SM4 algorithm
The SM4 algorithm is a grouping algorithm used in wireless LAN products. The block length of this algorithm is 128 bits, and the key length is 128 bits. Both the encryption algorithm and the key expansion algorithm use 32 rounds of nonlinear iterative structure. The structure of the decryption algorithm is the same as that of the encryption algorithm, except that the round keys are used in the reverse order, and the decryption round key is the reverse order of the encryption round key.
SM7 algorithm
The SM7 algorithm is a block cipher algorithm with a block length of 128 bits and a key length of 128 bits. The algorithm text for SM7 is not currently publicly available.
SM9 algorithm
SM9 is a pair-based identification cryptographic algorithm, similar to SM2, including four parts: general principles, digital signature algorithm, key exchange protocol, key encapsulation mechanism and public key encryption algorithm.
Currently, the software and hardware cryptographic products that support the national cryptographic algorithm include SSL gateways, digital certificate authentication systems, key management systems, financial data encryption machines, signature verification servers, smart cryptographic keys, smart IC cards, and PCI cryptographic cards. However, commonly used operating systems, browsers, network equipment, load balancing equipment and other software and hardware products still do not support domestic cryptographic algorithms. Restricted by the compatibility of the national secret algorithm, the application of the national secret algorithm is still lagging behind in the application of HTTPS encryption.
Comparison between GmSSL certificate and traditional SSL certificate
algorithm
Traditional SSL certificates are usually the RSA algorithm (2048 bits), which is currently the most influential and commonly used public key encryption algorithm and can resist the vast majority of known cryptographic attacks. However, with the rapid development of cryptography, it has been confirmed that the 1024-bit RSA algorithm has the risk of being attacked, and it has been upgraded to the 2048-bit RSA algorithm.
The current state secret SM2 certificate uses the ECC algorithm (256 bits), which was released by the State Cryptography Administration in December 2010. It is a public key cryptographic algorithm independently designed by my country, and is improved on the basis of elliptic curve cryptography. Its encryption strength is higher than the RSA algorithm (2048 bits).
Safety performance
Although the RSA algorithm still occupies a mainstream position in the current SSL certificate market, with the development of computer technology and the improvement of factorization, it has become possible to attack low-digit keys.
At present, the SM2 algorithm based on the ECC algorithm generally uses a 256-bit key length, and its unit security strength is relatively high, which is difficult to achieve in engineering applications, and the difficulty of deciphering or solving is basically exponential. Therefore, the ECC algorithm can provide higher security strength than the RSA algorithm with less computing power, while the required key length is much lower than that of the RSA algorithm.
In addition, in order to continuously improve the security strength, the key length must be increased. The ECC algorithm key length grows slowly (for example: 224-256-384), while the RSA algorithm key length needs to grow exponentially (for example: 1024-2048 -4096).
transfer speed
During communication, longer keys mean more data must be sent back and forth to authenticate the connection. Compared with the 2048-bit RSA algorithm, the 256-bit SM2 algorithm can transmit less data, which means less transmission time. Tested by relevant foreign authorities, the SM2 algorithm is used in the Web server, and the response time of the new concurrent processing of the Web server is more than ten times faster than that of the RSA algorithm.
When the national secret algorithm was designed, RSA2048 was the mainstream signature algorithm, so ECDSA and other algorithms will not be discussed here.
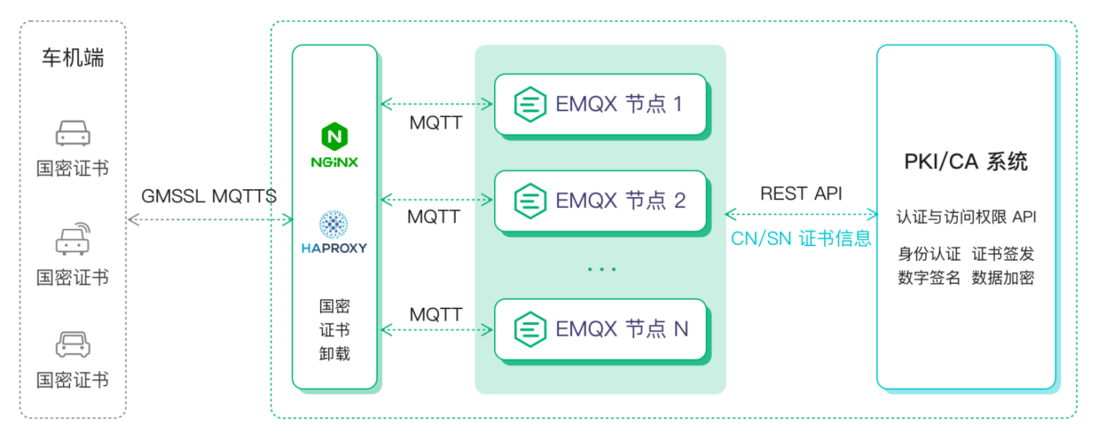
Application of National Secret Algorithm in Vehicle-Cloud Communication
The national secret algorithm is mainly used to encrypt and decrypt the transmission protocol in the vehicle cloud communication: the vehicle terminal is used as the sender, and the general data is encrypted by SM4, the content is digested by SM3, and then the digest is signed by SM2; As the receiver, the message broker first uses SM2 to verify the signature of the digest. After the signature verification is successful, it can prevent denial. It performs SM3 digest on the sent content to confirm whether the generated digest is consistent with the verified digest, which is used for anti-repudiation. tamper. In addition, SM4 requires the same key for encryption and decryption, and the same key can be generated by writing a key exchange module for SM4 symmetric encryption.
A few more things to note about asymmetric algorithms:
- The public key is generated from the private key;
- Public key encryption, private key decryption is the process of encryption
- Private key encryption, public key decryption is the process of signing;
Since the packet size of SM4 encryption and decryption is 128 bits, when the message is encrypted and decrypted, if the message length is too long, it needs to be grouped, and if the message length is insufficient, it needs to be filled.
EMQ transmission encryption authentication integration scheme based on national secret algorithm
Currently EMQ supports two national secret certificate integration schemes.
One is to develop a national secret authentication Java Gateway through plug-ins on EMQX;
The other is to compile and extend the native Nginx/HAProxy two mainstream LB proxy software through the GmSSL SDK in C language, so that it has the ability of GmSSL certificate authentication and uninstallation. This scheme is our more recommended.
Below we will introduce how to use two kinds of proxy software to solve the national secret certificate support.
Nginx compile extension GmSSL
- Unzip GmSSL:
tar -xvf gmssl_opt_xxx.tar.gz -C /usr/local - Unzip nginx:
tar -xvf nginx-x.xxx.tar.gz - Enter the
cd [nginx-x.xxx](http://nginx-1.xxx/)directory - Edit
auto/lib/openssl/conf, change all$OPENSSL/.openssl/to$OPENSSL/and save Build configuration
./configure \ --prefix=/usr/local/nginx \ --sbin-path=/usr/local/nginx/sbin/nginx \ --conf-path=/usr/local/nginx/conf/nginx.conf \ --error-log-path=/usr/local/nginx/log/nginx/error.log \ --http-log-path=/usr/local/nginx/log/nginx/access.log \ --pid-path=/var/run/nginx.pid \ --lock-path=/var/run/nginx.lock \ --http-client-body-temp-path=/usr/local/nginx/client_temp \ --http-proxy-temp-path=/usr/local/nginx/proxy_temp \ --http-fastcgi-temp-path=/usr/local/nginx/fastcgi_temp \ --http-uwsgi-temp-path=/usr/local/nginx/uwsgi_temp \ --http-scgi-temp-path=/usr/local/nginx/scgi_temp \ --without-http_gzip_module \ --with-http_ssl_module \ --with-http_realip_module \ --with-http_addition_module \ --with-http_sub_module \ --with-http_dav_module \ --with-http_flv_module \ --with-http_mp4_module \ --with-http_random_index_module \ --with-http_secure_link_module \ --with-http_stub_status_module \ --with-http_auth_request_module \ --with-threads \ --with-stream \ --with-stream_ssl_module \ --with-http_slice_module \ --with-mail \ --with-mail_ssl_module \ --with-file-aio \ --with-http_v2_module \ --with-openssl=/usr/local/gmssl \ --with-cc-opt="-I/usr/local/gmssl/include" \ --with-ld-opt="-lm"- Compile and install:
make install -
/usr/local/nginxis the generated nginx directory Configure
nginx.conf: go to the/usr/local/nginxdirectory, add inconf/nginx.conf:include /usr/local/nginx/conf/mqtt_tcp.confAdd the mqtt_tcp.conf file with the following content:
One-way authentication
stream { log_format proxy '$remote_addr [$time_local] ' '$protocol $status $bytes_sent $bytes_received ' '$session_time "$upstream_addr" ' '"$upstream_bytes_sent" "$upstream_bytes_received" "$upstream_connect_time"'; access_log /usr/local/nginx/log/tcp-access.log proxy; open_log_file_cache off; upstream mqtt_tcp_server { server 192.168.0.239:1883; #高可用均衡配置 #server 172.17.0.4:1883; } server { listen 1883; #监听端口 也可以使用 1883 #ssl_verify_client on; # proxy_connect_timeout 150s; # proxy_timeout 350s; # proxy_next_upstream on; proxy_pass mqtt_tcp_server; #反向代理地址 # proxy_buffer_size 3M; #tcp_nodelay on; proxy_protocol on; } server { listen 8083 ssl; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:AES128-SHA:DES-CBC3-SHA:ECC-SM4-CBC-SM3:ECDHE-SM4-GCM-SM3; ssl_verify_client off; ssl_certificate /usr/local/nginx/cert/Tsp_Server_Test_210906_sign.cer; ssl_certificate_key /usr/local/nginx/cert/Tsp_Server_Test_210906_sign.key; ssl_certificate_key /usr/local/nginx/cert/Tsp_Server_Test_210906_enc.key; ssl_certificate /usr/local/nginx/cert/Tsp_Server_Test_210906_enc.cer; proxy_pass mqtt_tcp_server; proxy_protocol on; } }Two-way authentication
Note: Two-way authentication has more ssl_client_certificate than one-way authentication: this is a CA certificate, which combines the signature CA and the key CA into one file, and ssl_verify_client is set to on.
stream { log_format proxy '$remote_addr [$time_local] ' '$protocol $status $bytes_sent $bytes_received ' '$session_time "$upstream_addr" ' '"$upstream_bytes_sent" "$upstream_bytes_received" "$upstream_connect_time"'; access_log /usr/local/nginx/log/tcp-access.log proxy; open_log_file_cache on; upstream mqtt_tcp_server { server 192.168.0.239:1883; #高可用均衡配置 #server 172.17.0.4:1883; } server { listen 1883; #监听端口 也可以使用1883 #ssl_verify_client on; # proxy_connect_timeout 150s; # proxy_timeout 350s; # proxy_next_upstream on; proxy_pass mqtt_tcp_server; #反向代理地址 # proxy_buffer_size 3M; #tcp_nodelay on; proxy_protocol on; } server { listen 8083 ssl; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:AES128-SHA:DES-CBC3-SHA:ECC-SM4-CBC-SM3:ECDHE-SM4-GCM-SM3; ssl_verify_client on; ssl_client_certificate /usr/local/nginx/cert/ca.pem; ssl_certificate /usr/local/nginx/cert/Tsp_Server_Test_210906_sign.cer; ssl_certificate_key /usr/local/nginx/cert/Tsp_Server_Test_210906_sign.key; ssl_certificate_key /usr/local/nginx/cert/Tsp_Server_Test_210906_enc.key; ssl_certificate /usr/local/nginx/cert/Tsp_Server_Test_210906_enc.cer; proxy_pass mqtt_tcp_server; proxy_protocol on; } }
start up
Operate under
/usr/local/nginxBoot:
./sbin/nginxReboot:
./sbin/nginx -s reloadStop:
./sbin/nginx -s stopVerify that the configuration file is correct:
./sbin/nginx -t
HAProxy integrates GmSSL compilation extension
- Unzip GmSSL:
tar -xvf gmssl_opt_xxx.tar.gz -C /usr/local - Unzip HAProxy:
tar -xvf haproxy_xxx.tar.gz Enter the HAProxy installation directory (not the same directory as the running directory generated by the later compilation) to modify
Modify the makefile:
Notes:
#OPTIONS_LDFLAGS += $(if $(SSL_LIB),-L$(SSL_LIB)) -lssl -lcryptoAdded:
OPTIONS_LDFLAGS += $(SSL_LIB)/libssl.aOPTIONS_LDFLAGS += $(SSL_LIB)/libcrypto.a -lm -lpthread -ldlModify the source code:
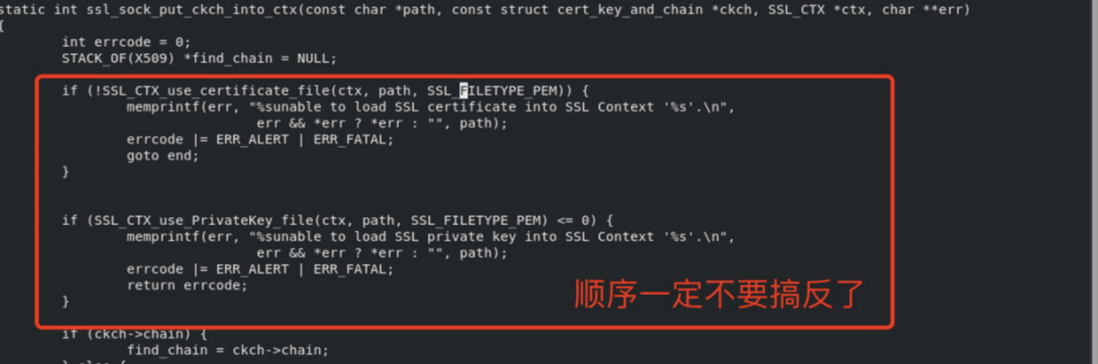
File src/ssl_sock.c Note: The red content cannot be modified directly, and the location needs to be changed, in the order of modification
The function ssl_sock_put_ckch_into_ctx puts the following code
if (SSL_CTX_use_PrivateKey(ctx, ckch->key) <= 0) { memprintf(err, "%sunable to load SSL private key into SSL Context '%s'.\n", err && *err ? *err : "", path); errcode |= ERR_ALERT | ERR_FATAL; return errcode; if (!SSL_CTX_use_certificate(ctx, ckch->cert)) { memprintf(err, "%sunable to load SSL certificate into SSL Context '%s'.\n", err && *err ? *err : "", path); errcode |= ERR_ALERT | ERR_FATAL; goto end; }change into:
if (!SSL_CTX_use_certificate_file(ctx, path, SSL_FILETYPE_PEM)) { memprintf(err, "%sunable to load SSL certificate into SSL Context '%s'.\n", err && *err ? *err : "", path); errcode |= ERR_ALERT | ERR_FATAL; goto end; } if (SSL_CTX_use_PrivateKey_file(ctx, path, SSL_FILETYPE_PEM) <= 0) { memprintf(err, "%sunable to load SSL private key into SSL Context '%s'.\n", err && *err ? *err : "", path); errcode |= ERR_ALERT | ERR_FATAL; return errcode; }
compile
You may need to install related dependencies in advance before compiling:
yum install pcre-devel zlib-develmake TARGET=linux31 USE_PCRE=1 USE_OPENSSL=1 USE_ZLIB=1 USE_CRYPT_H=1 USE_LIBCRYPT=1 SSL_INC=/root/gmssl/gmssl/include SSL_LIB=/root/gmssl/gmssl/libNote: SSL_INC and SSL_LIB specify the path where gmssl is decompressed
Install
make install PREFIX=/usr/local/haproxyNote: PREFIX=/usr/local/haproxy is the running directory generated by compilation, not the same directory as the installation directory.
configure
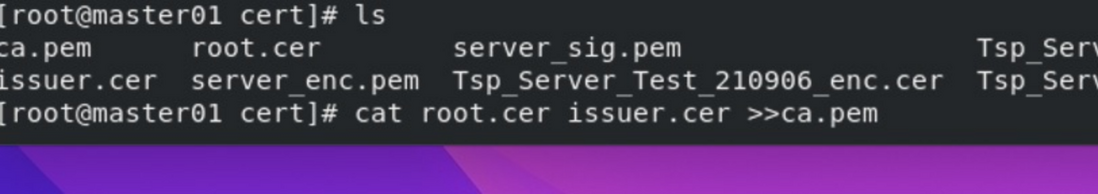
Certificate preparation:
Merge the signed certificate pem file and the signed private key pem file into XXX_sig.pem, the file name must end with sig.pem
Combine the encrypted certificate pem file and encrypted private key pem file into XXX_enc.pem, the file name must end with enc.pem
XXX_enc.pem will be loaded implicitly and must be placed in the same directory as XXX_sig.pem, eg: /usr/local/keystore/server_enc.pem
When mutual authentication is required: Combine CA certificates into one file (optional)
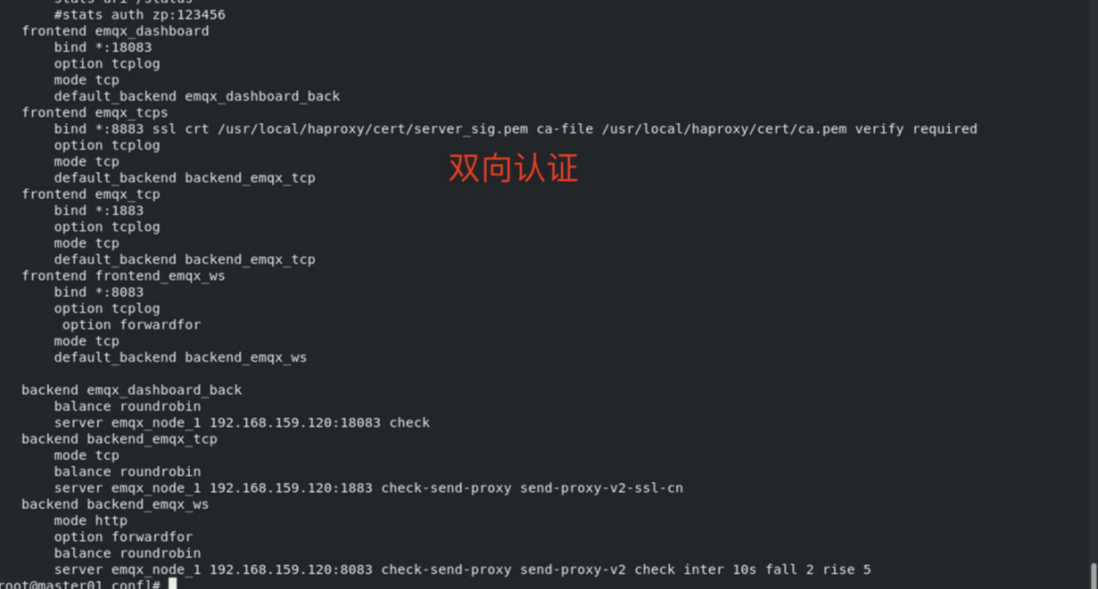
HAProxy.conf:
global daemon ssl-default-bind-ciphers ECC-SM4-CBC-SM3:ECC-SM4-GCM-SM3 #ssl-default-bind-options no-sslv3 maxconn 256 log 127.0.0.1 local7 info defaults mode tcp log global option tcplog timeout connect 5000ms timeout client 50000ms timeout server 50000ms stats uri /status #stats auth zp:123456 frontend emqx_dashboard bind *:18083 option tcplog mode tcp default_backend emqx_dashboard_back frontend emqx_tcps bind *:8883 ssl crt /usr/local/haproxy/cert/server_sig.pem ca-file /usr/local/haproxy/cert/ca.pem verify required option tcplog mode tcp default_backend backend_emqx_tcp frontend emqx_tcp bind *:1883 option tcplog mode tcp default_backend backend_emqx_tcp frontend frontend_emqx_ws bind *:8083 option tcplog # option forwardfor mode tcp default_backend backend_emqx_ws backend emqx_dashboard_back balance roundrobin server emqx_node_1 192.168.92.120:18083 check backend backend_emqx_tcp mode tcp balance roundrobin server emqx_node_1 192.168.92.120:1883 check-send-proxy send-proxy-v2-ssl-cn backend backend_emqx_ws mode http option forwardfor balance roundrobin server emqx_node_1 192.168.92.120:8083 check-send-proxy send-proxy-v2 check inter 10s fall 2 rise 5start test
If the configuration file is placed under:
/usr/local/haproxy/conf/Start command:
/usr/local/haproxy/sbin/haproxy -f /usr/local/haproxy/conf/haproxy.cfg
Epilogue
This article introduces the basic background knowledge of the national secret algorithm and its application in the Internet of Vehicles scenario. At the same time, it introduces the EMQ transmission encryption and authentication integration scheme based on the national secret algorithm. Through the configuration and operation examples provided in this article, readers can try to use it in the car. The national secret authentication is used in the networking platform to further increase the security of the platform.
The EMQ Internet of Vehicles GmSSL integrated solution closely meets the urgent needs of the Internet of Vehicles industry for network security and data security, and provides a strong guarantee for the security of Internet of Vehicles communication. At present, it has been deployed and applied in multiple vehicle-cloud security communication scenarios such as security certification of the Internet of Vehicles platform and V2X vehicle-road collaboration.
Copyright statement: This article is original by EMQ, please indicate the source when reprinting.




**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。