"How the Network is Connected" Reading Notes - Understanding the Basic Concepts of Networks (1)
talk about history
On August 6, 1991, British physicist Tim Berners-Lee, working at the Centre for Nuclear Research (CERN) in Geneva, Switzerland, formally proposed the World Wide Web, which is now our very familiar www.
what is www? World Wide Web WWW is the abbreviation of World Wide Web, also known as Web, 3W and so on. WWW is an integrated technology of information discovery technology and hypertext based on client / server approach.
I am curious here that we are talking about 3w and 3w every day, but the book on how the Internet appeared does not explain it?
Here I checked the online information and explained it according to my personal understanding:
In fact, the first signs of the Internet appeared in the APRA scientific research department established by the United States during the Cold War between the United States and the Soviet Union. The scientific research department that was suddenly torn out was scattered, and the scientific research work against the Soviet Union did not make much progress until a buddy named Robert Taylor When he appeared, his breakthrough was to discover that small communication networks were not compatible with different types of computers. We all know that the pinnacle of technology is to set rules. There is no doubt that he chose to build a set of protocols so that all computers can work in compliance with this set of rules. .
So he found a few awesome bosses and started to fiddle. In the middle, Balabala did a lot of things and went around a lot. The purpose was actually to achieve the above-mentioned things. In the end, in a failed "LOGIN" verification, although only the transmission The two letters "LO" were disconnected, but this failure was a historic progress, because the two different devices were really communicating, and the normal transmission of these five letters was completed after the final repair.
The ARPANET project, which was subsequently enacted, was the official prototype of the Internet.
This is the end of the extracurricular knowledge. Now let's look at the main points of the first chapter:
- How to parse the url?
- How does a DNS server query the IP address corresponding to a domain name?
- How does the DNS server relay?
- How does the browser delegate messages to the operating system to send to the web server?
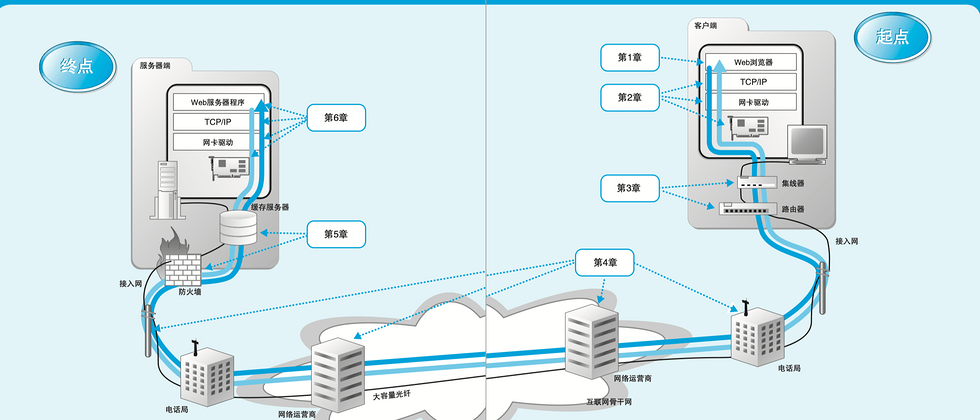
The core is to understand the role and role of DNS, and how browsers interact with DNS to complete the operation of resolving URLs (domain names) into IPs. The delegation process at the end of this chapter is the key content of the entire second chapter, and the notes are placed naturally. In the notes of Chapter 2, the notes are summarized into the second part for the convenience of understanding.
How to parse URLs
Let's start with URL, what is URL, URL is the abbreviation of Uniform Resource Locator, professional explanation is called Uniform Resource Locator, in addition to our common http and https protocols, browsers can also upload ftp files, download files, send electronic files Mail, browse new cultures, etc.
We regard these behaviors as resource interactions. Although there are different URL combinations for different resource interactions, no matter how the combination of URLs changes, the beginning determines everything , and the beginning determines how to treat resources.
To parse the URL we can see the following example:
When the file name is omitted, there are usually the following:
-
http://xxxx/dir/means that the content after/dir/is omitted. In this case, the actual access path corresponding to this directory is usually set for completion . - For the most classic in the web
http://localhost:8080/access path, usually the web server will access the file/index.html, if not, it will return a 404 page. - If there is only a domain name, such as
www.baidu.com, it will directly access the resources and related files corresponding to the root path set by the web server. - Ambiguous paths such as
http://localhost:8080/wishlistwill be processed according to whether it is a file name first, and then whether it is a directory, or as a request mapped to another resource, or a redirection .
The above content does not need to go into depth, just need to understand that the first job of the browser is to parse the URL .
HTTP request
The http request can be simply summed up in one sentence: what kind of operation is done on what , the so-called what refers to the URL, which means the identified target object, what kind of operation is done is the so-called method, and the method is mainly divided into For two POST and GET methods, other methods are basically useless, I have only encountered PUT and HEAD method.
GET Method: It is usually used to access some visible resources, or access to open resources. Usually, you can directly find the required resources in the specific directory without too many restrictions.
POST Method: It is more common to use a form or AJAX to access, and usually points to a WEB application. To get the data of the application, you need to pass some valid parameters required by the server, otherwise the server will The specific situation informs the client that the client does not have access.
AJAX stands for " Asynchronous JavaScript and XML " (asynchronous JavaScript and XML technology), which refers to a set of browser- side web development technologies that integrates multiple technologies. The concept of Ajax was proposed by Jesse James Jarrett [1] .
Http request message
Knowing what to do and what to do , let's take a look at how Http does this.
The Http request message is mainly divided into the following organizational structure:
- The first part of the first line extracts the content of the URL and parses it intact, and the HTTP version number at the end mainly marks the current HTTP request version.
For example: GET /cgi/sample.cgi?Field1=ABCDEFG&SendButton=SEND HTTP/1.1The second line is the message header, here are some simple contents:
- Data : Request response generation date.
- Pragma : Whether the data is allowed to be cached.
- Transfer-Encoding : Message body encoding format (important).
- Via : proxies and gateways to go through.
- There is a perfect blank line with no content after the header.
- The fourth behavior is the message body, but the experiment uses the GET method, so the content is usually empty.
Let's take visiting Google as an example. The following content is a reference to a request for accessing the Google search page. The content here is copied directly through F12 of Google Chrome. You can see that the request line, message header and message line are basically included (GET usually does not have so Not shown below) three.
常规
1. 请求网址:https://www.google.com/
2. 请求方法:GET
3. 状态代码:200
4. 远程地址:127.0.0.1:7890
5. 引荐来源网址政策:origin
请求标头
1. :authority:www.google.com
2. :method:GET
3. :path:/
4. :scheme:https
5. accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
6. accept-encoding:gzip, deflate, br
7. accept-language:zh,zh-TW;q=0.9,en-US;q=0.8,en;q=0.7,zh-CN;q=0.6
8. cache-control:no-cache
9. cookie:SID=KQi0QVpC_wxTynb6H6HjGmVq-9mYvCuIDOMx9EmEUJ8ii7dJzN_1F-ho69FdK6AN9ekOkA.; __Secure-1PSID=KQi0QVpC_wxTynb6H6HjGmVq-9mYvCuIDOMx9EmEUJ8ii7dJaTdIpqSfRfNb-BvF0haitA.; __Secure-3PSID=KQi0QVpC_wxTynb6H6HjGmVq-9mYvCuIDOMx9EmEUJ8ii7dJ6_WQQeEF09oAZ9MQfe21sA.; HSID=AOdmIhuBCutDeMwVS; APISID=ckyVXTB27QMaC2gQ/AVulr1cMnMbpD0e1x; SSID=AL0-0R0Ofsj3zaqrr; SAPISID=dqpTwJeh7bnii2Ki/AfsaDUfE8uMVR1aqv; __Secure-1PAPISID=dqpTwJeh7bnii2Ki/AfsaDUfE8uMVR1aqv; __Secure-3PAPISID=dqpTwJeh7bnii2Ki/AfsaDUfE8uMVR1aqv; SEARCH_SAMESITE=CgQIvJUB; 1P_JAR=2022-05-24-23; AEC=AakniGOKhznRpAD797X4u508i2XHJjEVYQQHANlqaJC2JSZ1F7mAe-vX_rg; NID=511=K-qt_LW-4ad1IYdJgfPLZjJw772wez2L3_FK9hwrrHAaksdhT8bTqz4icJEnJviOb92zcnyfS4h7P8HB_Is0f_FebYTe_5DR3qFEclHS1R9N1P7r9pv7Z4p12341S72RZRfzIlQ3-CVZUqQKBm1Xy1i9fKwejMGHTPMY2hk02sA--ey8nAEyt1_A7SVMe0RvrEkPnVm88fBnyyyFMMSCeSG1oqYKeC2x7iHJ0GwdbEpeGojpMQyQxAn1jAdxyXbC0oko0rCFjYn7eUREz2A9KA; SIDCC=AJi4QfGQeW0y_3pnzuBs7KI-WabF5XR_-dQchpcoNUN_bRVICBknb39qNQhP4IklnPn6kW4M3d8; __Secure-3PSIDCC=AJi4QfFOaoqiWv0mqmOskkIKVYy_-QNOATkPOyhNt9B8BBTMnRqnv-0zdgVgBNmIJRwlzBS4x6U
10. pragma:no-cache
11. sec-ch-dpr:2
12. sec-ch-ua:" Not A;Brand";v="99", "Chromium";v="101", "Google Chrome";v="101"
13. sec-ch-ua-arch:"arm"
14. sec-ch-ua-bitness:"64"
15. sec-ch-ua-full-version:"101.0.4951.64"
16. sec-ch-ua-full-version-list:" Not A;Brand";v="99.0.0.0", "Chromium";v="101.0.4951.64", "Google Chrome";v="101.0.4951.64"
17. sec-ch-ua-mobile:?0
18. sec-ch-ua-model:""
19. sec-ch-ua-platform:"macOS"
20. sec-ch-ua-platform-version:"12.3.1"
21. sec-ch-ua-wow64:?0
22. sec-ch-viewport-width:1440
23. sec-fetch-dest:document
24. sec-fetch-mode:navigate
25. sec-fetch-site:same-origin
26. sec-fetch-user:?1
27. upgrade-insecure-requests:1
28. user-agent:Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36
29. x-client-data:CLG1yQEIkrbJAQijtskBCMS2yQEIqZ3KAQjYjMsBCJShywEI2+/LAQjmhMwBCNupzAEI/qrMAQjDrMwBCKSvzAEYqKnKARirqcoB
30. 已解码:message ClientVariations { // Active client experiment variation IDs. repeated int32 variation_id = [3300017, 3300114, 3300131, 3300164, 3313321, 3327576, 3330196, 3340251, 3342950, 3347675, 3347838, 3348035, 3348388]; // Active client experiment variation IDs that trigger server-side behavior. repeated int32 trigger_variation_id = [3314856, 3314859]; }response content
The response page is also similar. It needs to respond to the content information required by the request line, and at the same time inform itself what kind of request it is allowed to accept. If the target IP cannot be found, it will usually turn into a 404 result.
响应标头
1. accept-ch: Sec-CH-Viewport-Width
2. accept-ch: Sec-CH-Viewport-Height
3. accept-ch: Sec-CH-DPR
4. accept-ch: Sec-CH-UA-Platform
5. accept-ch: Sec-CH-UA-Platform-Version
6. accept-ch: Sec-CH-UA-Full-Version
7. accept-ch: Sec-CH-UA-Arch
8. accept-ch: Sec-CH-UA-Model
9. accept-ch: Sec-CH-UA-Bitness
10. accept-ch: Sec-CH-UA-Full-Version-List
11. accept-ch: Sec-CH-UA-WoW64
12. alt-svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000,h3-Q050=":443"; ma=2592000,h3-Q046=":443"; ma=2592000,h3-Q043=":443"; ma=2592000,quic=":443"; ma=2592000; v="46,43"
13. bfcache-opt-in: unload
14. cache-control: private, max-age=0
15. content-encoding: br
16. content-length: 43734
17. content-type: text/html; charset=UTF-8
18. date: Tue, 24 May 2022 23:24:59 GMT
19. expires: -1
20. server: gws
21. set-cookie: 1P_JAR=2022-05-24-23; expires=Thu, 23-Jun-2022 23:24:59 GMT; path=/; domain=.google.com; Secure; SameSite=none
22. set-cookie: AEC=; expires=Mon, 01-Jan-1990 00:00:00 GMT; path=/; domain=www.google.com
23. set-cookie: AEC=; expires=Mon, 01-Jan-1990 00:00:00 GMT; path=/; domain=.www.google.com
24. set-cookie: AEC=; expires=Mon, 01-Jan-1990 00:00:00 GMT; path=/; domain=google.com
25. set-cookie: AEC=; expires=Mon, 01-Jan-1990 00:00:00 GMT; path=/; domain=.google.com
26. set-cookie: SIDCC=AJi4QfEXTiPm1BcAx1gfQzXOs-hmdcHylOVoSbbpy8cUIlP7hNwwfnfo_E8ZdTY1JZli8AqYYWk; expires=Wed, 24-May-2023 23:24:59 GMT; path=/; domain=.google.com; priority=high
27. set-cookie: __Secure-3PSIDCC=AJi4QfFdxOIbJrwDKltt2sBRVFIcLOCyqQmgTSfYjXTYwqbhh0GPLcR9cxsgyaIh1j_GITbGeHc; expires=Wed, 24-May-2023 23:24:59 GMT; path=/; domain=.google.com; Secure; HttpOnly; priority=high; SameSite=none
28. strict-transport-security: max-age=31536000
29. x-frame-options: SAMEORIGIN
30. x-xss-protection: 0The response content is relatively simple, and the main focus is on the status code and response phrase in the first line of content, and whether the request execution result is successful or unsuccessful. In the above interactive content, it should be noted that Http requests strictly follow that one request corresponds to one response content.
Note: Only one URI can be written in one request message. If you need to get multiple files, you must send a separate request for each file.
"How to parse the URL?" This question is completed from the beginning to the end. Let's take a look at the next question "How does the DNS server query the IP address corresponding to the domain name?".
IP and DNS
First of all, let's look at what IP and DNS are. It seems that the browser is responsible for parsing the URL (domain name) and sending the request and response content. In fact, it does not have these functions. The browser actually needs to rely on the operating system to send and receive network requests. , and the modern network is basically the world of TCP/IP , so IP plays a key role, and DNS stores IP .
- IP: It can be compared to our actual specific location, such as XX road XX number, XX road (network number) corresponds to the number assigned to the entire subnet , and XX number (IP address) number is assigned to the subnet After obtaining the IP address of the computer, it is equivalent to locking the specific location of the current computer, and naturally it can be found.
- DNS: To put it bluntly, it is a site that stores the records of domain name and IP mapping. To obtain the real arrangement, the browser needs to find the DNS to know, because the domain name is allowed to be freely defined by the user, and the same domain name will be mapped to multiple IPs.
Let's first observe how the number of XX Road XX, that is, the IP address, is found.
The sender of the network needs to go through the hub first to forward the content to the nearest router through the subnet, and then the router will continue to cross to find the next router closer to the receiver, and finally find the hub and then forward it to the receiver's router. , the router is the steering wheel here, and DNS addressing is like navigation.
What are hubs and routers? A router: A device that forwards packets. B hub: a device that forwards packets, divided into two types: relay hub and switching hub.
Components of an IP Address
An IP address is a 32-bit bit number, divided into 4 groups by 8 bits, each group is represented in decimal and separated by a small dot.
However, it is impossible to locate the IP address and network number based on these 32 bits alone, so additional information needs to be added to the IP address.
Usually the combination of IP addresses has the following methods:
a) IP address subject: 11.22.33.44
b) IP and subnet mask: 11.22.33.44/255.255.255.0
c) The number of bits of the network number is expressed as the subnet mask: 11.22.33.44/24
d) Subnet address: 11.22.33.0/24 , which represents the entire subnet
e) Subnet broadcast address: 11.22.33.255/24
First of all, the entire IP is divided into 32-bit fixed length, each group of four is separated by dots, represented by the decimal system of 0 - 255, for example, 0 is 8 0s, 255 is 8 1s, but only by virtue of 32 digits is I can't tell which part of the 32 bits is the network number and which part is the host number, so the following is the basic composition of IP:
-
11.22.33.44: indicates the basic IP. -
11.22.33.44/255.255.255.0: The front part is the basic IP, and the latter part is the subnet mask, which is the same as the IP address. Note that the last 8 bits are all 0 to represent the entire subnet. -
11.22.33.44/24: This 24 is also the subnet mask, but the way to represent the subnet is to use the number of bits. -
11.22.33.0/24: The subnet mask has not changed, but the IP address has changed. The last 8 bits of 0 also represent the entire subnet. -
11.22.33.255/24: The subnet mask has not changed, but the IP address has changed. The last 8 bits are all 1 to broadcast the entire subnet.
What is a subnet mask?
It may be difficult for beginners to understand the concept. If you don't understand it, it is recommended to find more information and choose an understandable explanation (the key is to understand and repeat it yourself).
The following is the original picture from the book. After reading it, it is not particularly intuitive and I don’t know what to do, so I made a supplementary explanation.
In fact, the network number in the figure below uses AND (bit operation & ) to calculate the network number. After the calculation, it is confirmed that the network number is 10.1.2, and the omitted part is actually a mask of 8 0s. Mask the host, the subnet here is 10.1.2.0, and the corresponding host IP is 10.1.2.3.
If you don't understand what is said above, here is a supplementary explanation:
First of all, we need to know what the subnet mask is for. To put it bluntly, it is to divide the network number and the host number. The network number can be regarded as a building, and the host is a small room inside, but the room number may be 101 , or 0101 , more likely 00101 , depending on how many hosts can be assigned from 0000 to 111. And computer 0 is very special, so the part of the network number + the number of bits covered by the subnet mask (the performance is all 0) form a subnet, and only hosts on the same subnet can communicate with each other .
Therefore, the subnet mask cannot exist alone. It must be used in conjunction with the IP address . The subnet mask is mainly divided into two parts: all 1s represent the network number, and all 0s represent the host number.
Then we can just set a subnet mask such as 255.255.255.111 OK?
The answer is no , no , no . Because the subnet mask must be composed of consecutive 1s and 0s , the above mask 255.255.255.0 is the correct usage. For example, 255.255.255.244 is also a qualified subnet mask.
Let's illustrate with an example:
1100 0000.1010 1000.0000 0001.1000 0001 -- 192.168.1.129
1111 1111.1111 1111.1111 1111.0000 0000 -- 255.255.255.0
————————————————————
1100 0000.1010 1000.0000 0001.0000 0000 -- 划分出最终子网网段:192.168.1.0
注:确认最终的网络号和主机网段使用了位操作 & (1 & 1 = 1,1 & 0 = 0) Judging from the final result 192.168.1.0 the first 24 bits are exposed, and the last 8 bits are covered by the subnet mask, so his other way of writing is 192.168.1.0/24 , indicating that the 24 bits are 1 for the network number, and the remaining 8 bits are used to represent the host number but all are 0 because they are masked.
Although it is masked, it doesn't matter if the host number is 0 or 1. If the host number falls from 192.168.1.0 to 192.168.1.255 it means that the subnets in the same network segment are treated equally, for 192.168.1.129 Indicates that 129 bits are included in this network segment.
summary
- The subnet mask must be composed of consecutive 1s and 0s. The part of 1 is simply memorized to divide the network number, and the part of 0 is used to mask the host number. Hosts in the same subnet can communicate with each other.
- There are two ways to write the subnet mask: one is to use the same 32-bit full representation as the IP address, and the other is to use a number to calculate 1-bit number to replace, for example, 24 is the 24 1s in the figure below.
- The host number of the IP address. All 0s represent the entire subnet, and all 1s represent sending packets to all devices on the subnet. Here to add the case of all 1s - "broadcast".
What does broadcast mean? The broadcast address is an address specially used to broadcast to all hosts in the network at the same time, as long as the hosts on the same network segment can listen to the broadcast. (For example, the broadcast address of ---63065d0bd52ec5d4627180419ac306ee192.168.211.32/24is:192.168.211.255)
DNS
DNS: Domain Name System Domain Name Service System , the most common usage is to associate the server name with the IP address, of course, it is only its main business, and he has some side businesses that are also very important but not the key to be interested in.
IPs are hard to remember, while short domain names are easier to remember. You may think that a long domain name is difficult to remember. Although the speed of IP resolution is much faster than that of domain name resolution, it is obviously impossible for netizens to memorize a series of numbers in order to visit a website. At the same time, the domain name actually It is also meaningful for the development of the Internet at that time.
So who is going to tell the host what the real IP of the domain name is? At this time, DNS comes into play. The role of DNS is to put it bluntly, it is a thing used to map IP and domain names.
How does DNS complete the mapping? For the user host, there must be a client for resolving DNS. This client is usually called a resolver, and the process of resolving an IP address from a domain name is also called domain name resolution .
call the parser
So how to call the parser? The parser is actually a piece of program code. This piece of program code is contained in the Socket library of the underlying operating system. The parser is called through the Socket library, and then the parser will send a message to the DNS server. Query message, the DNS server queries IP according to the request and then returns a response message.
The process of Socket parsing domain name is very simple, it only needs one line of code to complete: gethostbyname(" www.lab.glasscom.com "); .
Libraries: Refers to a collection of general-purpose program components used to standardize the normative organization of program code. Taking the parser as an example, the Socket library is a collection of program components used to invoke network functions.
How does the parser work internally?
When the application calls the resolver, the control will be transferred to the resolver. After the control is transferred to the resolver, the resolver will generate a query message to be sent to the DNS server. The generation process is similar to constructing a "Please tell XXX's IP address" message, and send it to the DNS server to complete the resolution.
Pay special attention to note that the sending request is not completed by the resolver , but needs to be delegated to the protocol stack of the operating system again, so at this time, the authority will be transferred to the protocol stack again, and the protocol stack will finally send the message to the DNS through the network card, and then the DNS finds the The IP returns a message, and the DNS resolution request is completed at this point.
It is worth noting that the resolver will write the extracted IP address into the memory address specified by the application. In addition, it should be noted that the IP of the requesting DNS server itself also needs to be configured, but this IP address is set in advance as a TCP/IP project. OK, you can get it directly without further querying.
Finally, there are differences in the way of obtaining the address of the DNS server in different operating systems.
According to the above description, summarize the DNS resolution process:
- The WEB browser sends a domain name resolution request, and requests resolution to the resolver through Socket, and the application will hang at this time.
- The resolver is responsible for "translating" the application's DNS resolution requests, but delegates specific request operations to the system stack.
- The system stack is responsible for sending the request to the DNS server through the network card and waiting for the DNS feedback result.
- After DNS obtains the real IP, the result is sent back to the application through the reverse link.
DNS work
Next, let's see how dns works. dns needs to query user messages, which includes the following parts:
- Domain name: used to replace IP for easy memory.
- class: Considering the situation outside the Internet, of course, the external network now only has the Internet marked as in.
- type: Indicates that the record type is used to distinguish the dns parsing method. Different types have different results.
It should be noted that all records of type a are registered on DNS. For example, all mail types are of MX type. In fact, the entire DNS work is simply looking up the table according to the type and domain name, and returning the one that matches, otherwise, it will be sent back. will not be found.
Domain name level: The so-called domain name level means that DNS cannot be a single server, but requires the cooperation of multiple servers, each of which manages its own scope of content, and for a domain name, the part to the right is higher in the domain name level.
Does this seem a bit interesting? Taking daily life as an example is not what we think www is the highest, in fact, he is the lowest level, .com is the highest.
DNS lookup steps
First, register the IP addresses of the DNS servers responsible for managing subordinate domains with their superior DNS servers, then register the IP addresses of the superior DNS servers with the higher-level DNS servers, and so on.
举个例子, www.baidu.com ,DNS www.baidu.com 8870a71fcb0f8e9563236df8cfa7be77---整个域名注册到baidu.com , baidu.com Register to com domain name, and then register com to the root domain, so that you can find subordinates through superiors.
It is mentioned here that DNS has a root domain. The root domain name refers to a period . , which is similar to the Linux root path in terms of expression.
According to the root domain, it can be explained why any strange and other domain names can be accessed. The reason is that all subordinates will be registered to the superior, and finally have a common one. If all subordinates want to find the root domain, they naturally need to register the period of the root domain.
The process of DNS lookup is to find the nearest DNS from bottom to top and then from top to bottom to find the root domain. Go down to find the final ip, which is why it is slow to access foreign ip, because the routing link is really long, and it may take dozens of dns search to find.
DNS cache
If each host always needs to obtain the IP information corresponding to the domain name through DNS for each request, it is impossible to find it through DNS every time. In fact, the real IP resolved will be cached in advance and the repeated data will be returned directly for the next visit. That's it.
In addition, although the previous introduction is to search from top to bottom from the root domain to the bottom, in fact, DNS can also use the caching feature to speed up access speed through multiple levels of shared domain names, such as www.baidu.com www.baidu You can find it quickly by jumping two levels directly from the shared cache (of course, you can find the nearest DNS here, this is just an example).
However, caching has a side effect, that is, non-existing ip address messages will also be cached, but in order to prevent this situation, there is usually an expiration time. After the expiration, you still need to go through the DNS lookup process again.
problem guide: problem
- What does http in http://www.nikkeibp.co.jp/ stand for?
Indicates the HTTP protocol
- What's the difference between the two URLs below?
a. http://www.nikkeibp.co.jp/sample
b. http://www.nikkeibp.co.jp/sample/
The difference is that the sample may be parsed out of the expected results.
What is the address used to identify computers and servers connected to the Internet?
IP address
What is the name of the server used to query the IP address based on the web server's domain name?
DNHS server
What is the name of the program that sends the request message to the DNS server?
parser.







**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。