Author: Cai Wei
The middleware dble test members are mainly responsible for the daily testing of dble, and are keen to explore and learn new technologies.
Source of this article: original contribution
*The original content is produced by the open source community of Aikesheng, and the original content shall not be used without authorization. For reprinting, please contact the editor and indicate the source.
Introduction to SSL Protocol
As we all know, if we use clear text when transmitting data on the network, data will be easily monitored and stolen, which will cause certain security problems. This is undoubtedly the data security of some sensitive personal information and even the company. caused a great risk.
Based on this, there is bound to be a certain demand to "package" the data transmitted on the network, and SSL came into being under this background. Netscape proposed the security protocol SSL in 1996, which is a protocol that works between the application layer and the transport layer. The design is comprehensive, and it involves many concepts, not only "packaging" data [data encryption], but also It provides authentication and message integrity verification mechanisms, and has made great contributions to the construction of network data transmission security, thereby greatly improving the security of the Internet.
For the database level, encrypted communication is also very important. After all, the data storage of any business must eventually be implemented on the database, and its importance is self-evident. So for MySQL, SSL is already a mature function and widely used. The protocol implementation principle and encryption algorithm are no longer the focus of this article, so I won't repeat them here. You can refer to the historical public account article: MySQL : Analysis of SSL Connections
DBLE of SSL
Overview
As a database middleware product, when using DBLE, after mounting MySQL to the DBLE backend, you can completely disconnect from MySQL and establish a direct connection with DBLE. So the question is, how to ensure the security of data when communicating with DBLE? Obviously, DBLE needs to learn from MySQL in this regard and arm itself with SSL to ensure the security of user data when communicating.
In the upcoming DBLE version, we will support SSL encrypted connections. It should be noted that the encryption process is currently in the Client-DBLE communication stage, and the DBLE-MySQL communication stage is not involved yet. At the same time, the small version of DBLE 3.22.01.1 that has been released has also taken the lead in supporting SSL. Interested students can download the relevant version to try it out.
Instructions for use
The SSL connection configuration of DBLE is similar to that of MySQL, but it is not the same. The following is a brief introduction to the configuration and use of DBLE for SSL encryption.
Students who are familiar with SSL should know that the premise of using SSL must be various certificates [involving various key information], and DBLE is no exception. Self-signed certificates are used in MySQL. Self-signed certificates are digital certificates issued by untrusted CA agencies, that is, certificates issued by themselves. Unlike traditional digital certificates issued by trusted CAs, self-signed certificates are created, issued and signed by some companies or software developers. DBLE also uses the same method as MySQL: using the self-signed certificate method to make the SSL certificate.
Certificate making
Certificate creation needs to be done with the help of OpenSSL. If it is not installed on the machine, you can manually install OpenSSL.
1. Make a CA self-signed certificate (including public key) and private key
openssl genrsa 2048 > ca-key.pem
openssl req -new -x509 -nodes -days 3600 -key ca-key.pem -out ca.pem2. Create a private key and issue a digital certificate for the server
openssl req -newkey rsa:2048 -days 3600 -nodes -keyout server-key.pem -out server-req.pem
openssl rsa -in server-key.pem -out server-key.pem
openssl x509 -req -in server-req.pem -days 3600 -CA ca.pem -CAkey ca-key.pem -set_serial 01 -out server-cert.pem3. Create a private key and issue a digital certificate for the client (similar to above)
openssl req -newkey rsa:2048 -days 3600 -nodes -keyout client-key.pem -out client-req.pem
openssl rsa -in client-key.pem -out client-key.pem
openssl x509 -req -in client-req.pem -days 3600 -CA ca.pem -CAkey ca-key.pem -set_serial 01 -out client-cert.pem4. Verify whether the server and client digital certificates are credible. When the output result is OK, it means that the certificate is passed.
openssl verify -CAfile ca.pem server-cert.pem client-cert.pemIt is worth mentioning that the mysql_ssl_rsa_setup command that comes with one-click certificate generation is also roughly in accordance with the above to generate certificates, so it is more convenient to directly use mysql_ssl_rsa_setup to generate the corresponding certificate files [of course, it needs to be used for DBLE. Certificate type conversion, see below].
certificate type conversion
Since DBLE is developed based on the JAVA language, the certificate formats pem, crt and other formats generated by OpenSSL cannot be correctly recognized in the JAVA language, and additional use of the keytool tool [java comes with it natively, no need to install it after installing java] is required. p12, jks format, and if the client used is JDBC, the certificate used in the relevant URL also needs to use the converted certificate file, and other drivers are applicable to the pem certificate file.
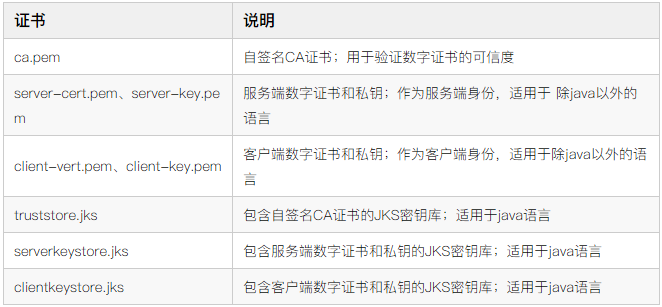
1. Import ca.pem into the keystore of the Java platform. Java supports keystore types: JKS, JCEKS, PKCS12, PKCS11 and DKS. Here, the truststore.jks keystore with the JKS extension is generated, and the password can be customized , defined here as 123456
keytool -import -noprompt -file ca.pem -keystore truststore.jks -storepass 1234562. Convert server-cert.pem and server-key.pem into p12 type keystore, and then convert them into JKS type keystore, the password can be customized, defined here as 123456
openssl pkcs12 -export -in server-cert.pem -inkey server-key.pem -out serverkeystore.p12 -passout pass:123456
keytool -importkeystore -srckeystore serverkeystore.p12 -srcstoretype PKCS12 -destkeystore serverkeystore.jks -srcstorepass 123456 -deststorepass 1234563. Similarly, convert the certificate file used by the client into a JKS type keystore. The password can be customized, which is defined as 123456 here.
openssl pkcs12 -export -in client-cert.pem -inkey client-key.pem -out clientkeystore.p12 -passout pass:123456
keytool -importkeystore -srckeystore clientkeystore.p12 -srcstoretype PKCS12 -destkeystore clientkeystore.jks -srcstorepass 123456 -deststorepass 123456So far, we have obtained the following key file information:
Server DBLE configuration
Server DBLE configuration
When using SSL, DBLE as a server needs to manually configure related file information and enable related functions. Consistent with MySQL, we provide a switch supportSSL to identify whether SSL is enabled. The default value is false. If you need to use SSL connection, you first need to ensure that this switch is turned on. At the same time, you need to configure some certificate information used, and configure the following in bootstrap.cnf:
-DsupportSSL=true
-DserverCertificateKeyStoreUrl=${path}/serverkeystore.jks
-DserverCertificateKeyStorePwd=123456
-DtrustCertificateKeyStoreUrl=${path}/truststore.jks
-DtrustCertificateKeyStorePwd=123456After the configuration is complete, restart dble.
In order to facilitate the query of some status information of SSL, we have added some metadata information for maintaining related SSL in the dble_information library of the DBLE management side. After ensuring that the configuration is correct and restarting dble, the corresponding SSL configuration information and status:
Client connection configuration
Different connection modes are distinguished when connecting to MySQL using SSL. This method is also applicable to DBLE. The following provides two common client configurations for Client encrypted connections:
experiment
disabled mode
Before connecting to DBLE with SSL encryption, let's use the packet capture tool wireshark to see how data transmission looks like when connecting to DBLE without encryption. Here is an example of using JDBC as the client. Before querying, the author has followed the above steps to configure and enable SSL on the DBLE side, created the user table, and prepared relevant data, which will not be discussed here as a key point.
1. Non-encrypted connection to DBLE, the following is the JDBC Demo for reference, establish a connection with DBLE and query the user table data:
public class SslTest {
private static final String JDBC_DRIVER = "com.mysql.jdbc.Driver";
public static void main(String[] args) throws SQLException, IOException, ClassNotFoundException {
List<User> res = disabled();
System.out.println(res);
}
public static List<User> disabled() throws ClassNotFoundException, IOException, SQLException {
List<User> usersList = new ArrayList<>();
Properties pro = new Properties();
FileInputStream fis = new FileInputStream("E:\\jdbc\\src\\main\\resources\\dble.properties");
pro.load(fis);
Class.forName(JDBC_DRIVER);
String url = "jdbc:mysql://" + pro.getProperty("host") + ":" + pro.getProperty("port") + "/" + pro.getProperty("db");
String fullUrlString = url + "?useSSL=false"; // 非加密连接
Connection conn = DriverManager.getConnection(fullUrlString, pro.getProperty("user"), pro.getProperty("password"));
PreparedStatement ps = conn.prepareStatement("select username from user");
ResultSet rs = ps.executeQuery();
while(rs.next()){
String name = rs.getString("username");
usersList.add(new User(name));
}
ps.close();
rs.close();
conn.close();
return usersList;
}
}2. After the packet capture is enabled, execute the relevant demo to query, and filter and parse the packets as follows:
It can be found that the transmitted data, including login information, SQL and returned data information, can be queried in plaintext after being parsed by wireshark.
required mode
Here, only a certain SSL encryption mode is used as an example for test demonstration-required. After a slight modification in the above JDBC Demo, the URL parameter is changed to the corresponding mode parameter [as shown below], and encrypted communication can be performed:
String fullUrlString = url
+ "?useSSL=true&requireSSL=true&verifyServerCertificate=false";Then capture the packet again and execute Demo to query, parse the packet and filter to get:
It can be found that after the establishment of the TCP connection, the SSL protocol will carry out the authentication process of both parties. For the specific protocol analysis, please refer to: https://www.jianshu.com/p/8028bcbc4e05 After authentication, the TLS encryption protocol standard will be used. After the data packets are encrypted and transmitted, the transmitted data information cannot be obtained even after preliminary analysis, which ultimately ensures the security of the data. Of course, if we have the SSL key file of the server, adding the relevant key information in the wireshark SSL protocol settings can also successfully parse out the specific packet information transmitted. Test yourself.
Summarize
Everything has two sides. Although encrypted connection ensures the security of data, on the other hand, it undoubtedly sacrifices some performance. From the perspective of SSL implementation, operations such as handshake, encryption, and decryption are required when establishing a connection. Therefore, the time-consuming is basically in the stage of establishing the connection, which may not be very friendly to applications using short connections, because there will be a large performance loss. However, it may be much better for applications that use connection pooling or long connections. Therefore, for applications that require high performance, or applications that do not generate core sensitive data, performance and availability are the top priorities, and SSL is not recommended.
At the same time, it should be noted that the DBLE side does not set the [require_secure_transport] similar mandatory requirements to use the secure connection parameter setting when performing the SSL settings like MySQL, nor does it distinguish the applicable objects of the SSL configuration according to the user, as long as the DBLE service All users can choose whether to use SSL encrypted connection when establishing connection with DBLE.




**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。