Introduction: On the afternoon of June 30, Alibaba Cloud's WAF product will be upgraded to version 3.0. For the safety assurance work during important festivals or large-scale events, a special protection package for heavy protection scenarios will be released, which will be combined with the basic product capabilities to form A set of tens of millions of IP blacklists, one-click regional bans, and automatic update of scenario-based rules effectively protect against new vulnerabilities. At the same time, the open API capabilities will help realize an integrated solution for automated operation and maintenance.
Click to learn more about the release of Alibaba Cloud Web Application Firewall 3.0
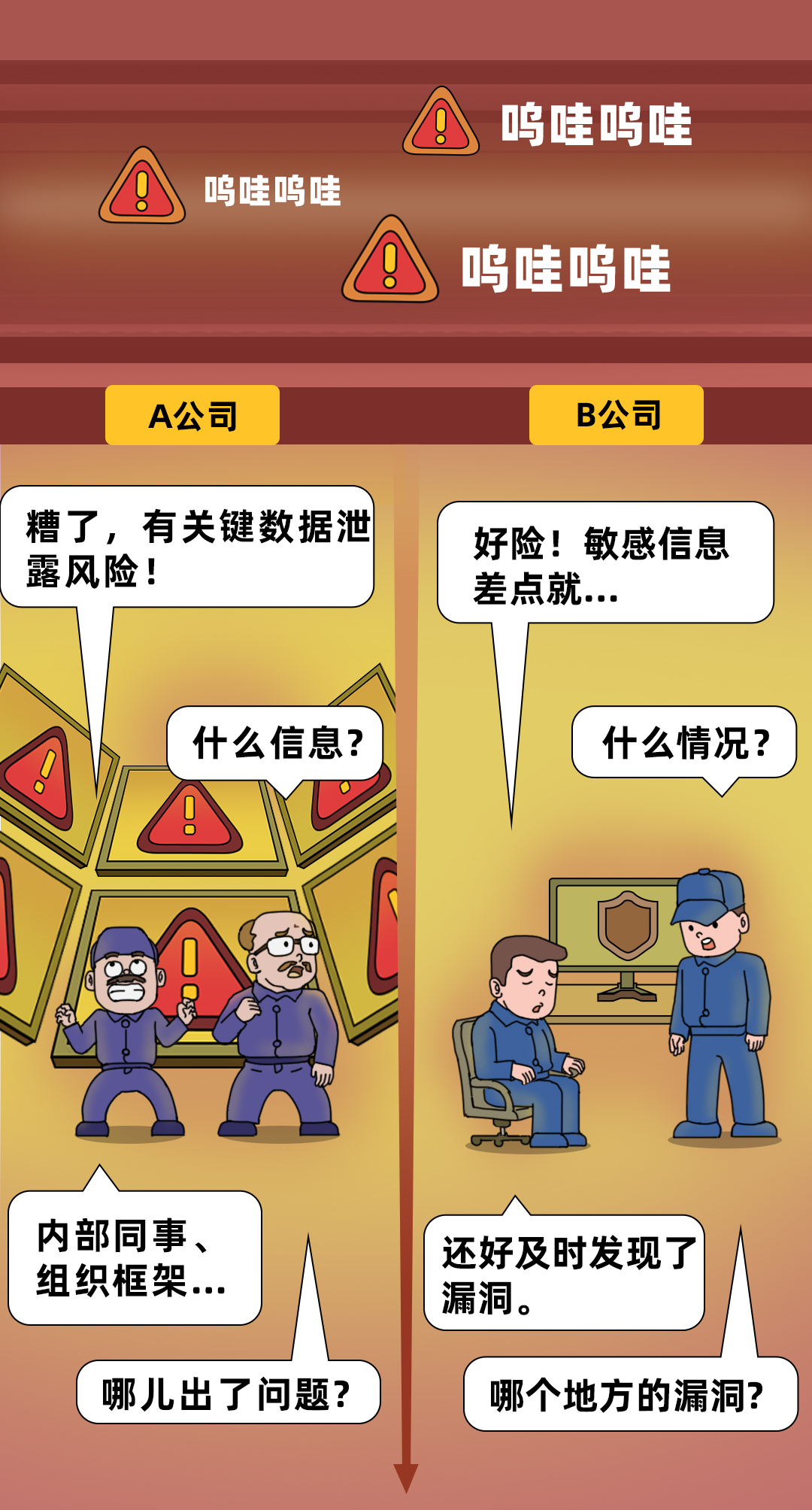
Improper configuration, internal interface exposed
The code logic is flawed and the authentication is not in place
data breach...
Why is API security increasingly important?
API is a pre-defined interface in the development process of some applications in order to facilitate mutual calls. For example, when you access a shopping platform through a WeChat applet, the applet needs to use the API to connect to the mall's inventory, order and other systems.
In the past, due to the lack of rich digital business, for an organization, the frequency of internal API development and calls was low, and there were fewer mutual calls with external systems and applications, so API was only a trivial existence in the complex IT system, and its security less attention.
But nowadays, more and more businesses have moved online. For organizations, providing services on the Internet needs to call more other external interfaces. The mutual calls of APIs between different enterprises and organizations inevitably increase the exposure of APIs. Safety is becoming more and more important.
The core risk caused by these risks is data leakage . With the successive promulgation and formal implementation of the "Data Security Law" and the "Personal Information Protection Law", APIs, as a core element in dealing with data, need to be focused on.
Where is it difficult for enterprises to do API security well?
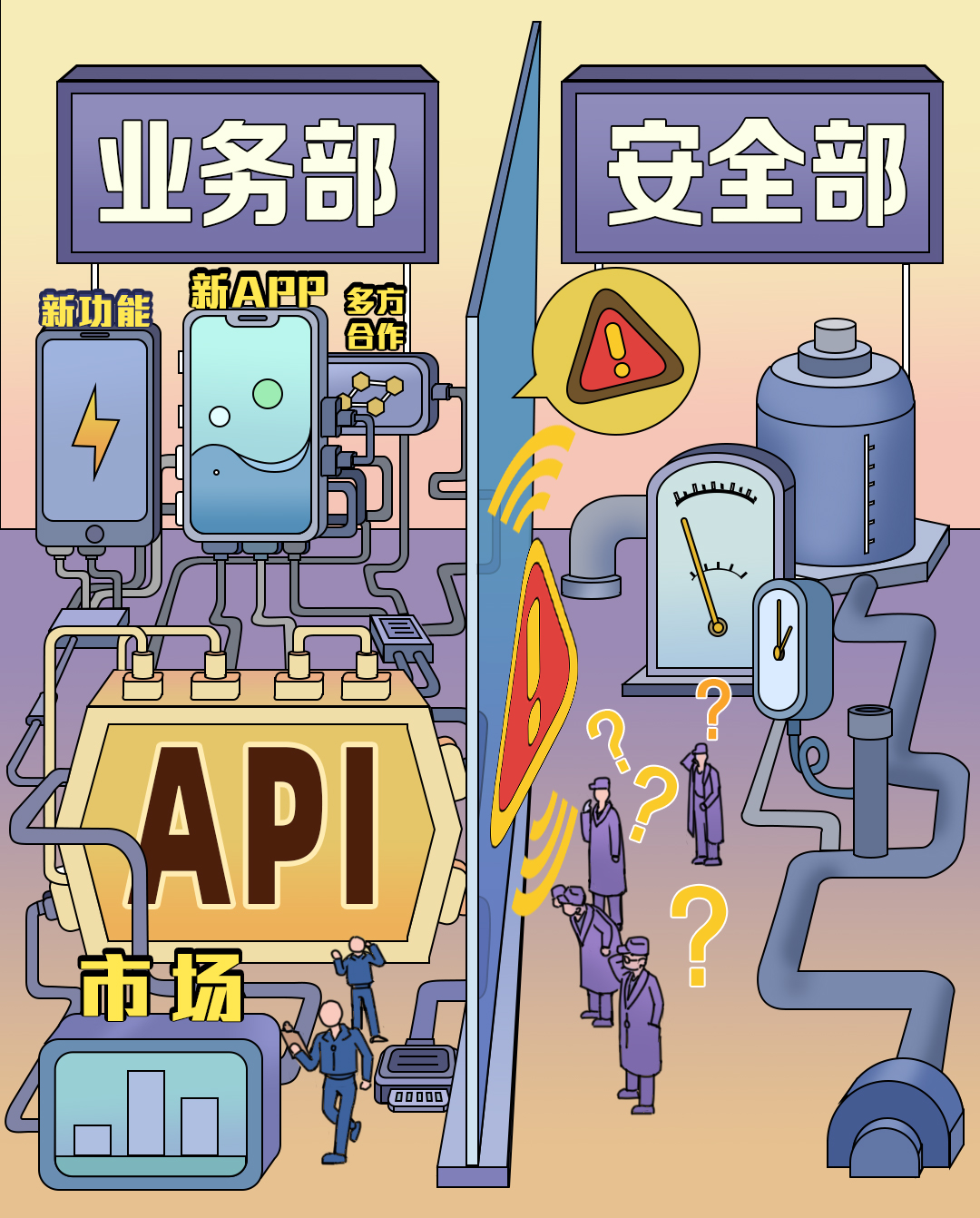
One of the characteristics of API is that it is closely related to the business logic, business scenarios, and complexity of the enterprise organization. With the rapid development of digital business, the number of APIs and security demands will increase directly.
Existing API assets are unclear, and new API interfaces are unknown
For traditional enterprises, the system is often very complex, and it is basically impossible to sort out which interfaces are called by whom; even emerging enterprises born from APIs that have attracted widespread attention are unlikely to check all interfaces before each version goes online. . Ideally, the business should go online only after it is confirmed that it is safe, but in fact it is mission impossible, and the risk is buried here.
In addition, the development and maintenance of APIs is usually the responsibility of the R&D team, while the security is the responsibility of the security team . The information between the two parties is poor , so that the traditional API gateway manually uploading interface information is bound to produce a large number of "fish that slip through the net".
Richer digital business brings more complex API management
Enterprise API security construction consumes a lot of loops, aggregate analysis, bandwidth, and computing resources. Every change in digital business may bring changes in the number of APIs, calling logic, and importance. There may be countless changes every day. API launch and failure , business changes cannot be rejected in order to ensure API security, nor can they cause security risks due to business changes. How to balance the two is a problem that must be solved.
Alibaba Cloud's native API security solution: high performance, ultra-controllable, extremely scalable, simple and efficient
Alibaba Cloud API Security is a comprehensive set of API security solutions built on the basis of Alibaba Cloud WAF products, which can fully cover OWASP API top 10 risk responses. One-click activation on WAF eliminates complex deployment costs, supports life cycle management of API assets, and can directly exert its native defense capabilities, form a closed-loop solution for malicious behavior disposal, reduce cross-product operation costs, and WAF product attacks Blocking capabilities, access frequency restrictions, crawler protection, account security special protection, security scanning protection, sensitive data leakage prevention and other capabilities can be used as API security disposal capabilities, and feature solutions are formed for specific scenarios.
(Data reference OWASP API Security Top 10)
Extreme zoom
Combined with Alibaba Cloud's global edge site network, it provides end users with the lowest possible API request and response latency. Limit traffic and authorize API calls to ensure backend operations can withstand traffic spikes and don't call backend systems unnecessarily.
If a customer has 5000QPS a day, millions of logs will be generated. It is unimaginable to check API risks from millions of logs by manpower. With the help of Alibaba Cloud model, automatic analysis can be completed within minutes;
easy monitoring
Monitoring performance metrics and information about API calls, data latency, and error rates from the Alibaba Cloud Control Panel helps customers monitor their own calls to services more intuitively. The optimization of the console, in terms of visual aspect, enables customers to have a clearer asset life cycle, more easily locate pre/alarm and new/old API online and offline situations, and more clearly analyze data risks.
From API asset discovery, risk vulnerability detection to abnormal behavior detection, the user only needs to confirm and handle the alarm;
Flexible control
There is no need to deploy detection nodes on the customer business side, and bypass static analysis is adopted, which has no impact on business and will not pollute business data. The Alibaba Cloud API security solution relies on cloud WAF, native access through cloud domain names, and static bypass analysis. Since all traffic passes through WAF, the full asset list of Web API assets can be viewed.
Minimalist and efficient
There is no need to configure one-click opening and cloud management. Make full use of the native advantages of the cloud, combined with business logic, without any cooperation or probes, you can find problems, observe details, and handle closed-loop one-click opening, while assisting in optimizing business logic.
[It is worth noting that the optimization of the API console capability this time makes the asset life cycle clearer, the problem location is more convenient, and the data problem is more obvious. 】
Through automatic analysis of API access logs, Alibaba Cloud creatively adds business tags to each API. From the three dimensions of "interface type + sensitivity level + authentication capability", it comprehensively defines the importance of API interfaces and implements classification and hierarchical management of APIs. .
At present, Alibaba Cloud provides nearly 20 types of business labels, which basically cover the common business types of customers.
Another benefit of API classification and hierarchical management is that it can assist in optimizing business logic. For example, in an anti-climbing scenario, if it is detected that an interface has been swiped, you can see the business scenario corresponding to the interface, so as to find out the homogeneous business scenario in the alarm and optimize it.
API Risk Vulnerability Identification
Alibaba Cloud API Security can identify security risks including brute force cracking and anti-climbing, and divide the risks into three levels based on the importance of the interface, covering the needs of different industries such as transportation, e-commerce, finance and insurance, and catering and retail.
At the same time, it can actively and timely discover the natural API exposure risk in development and design, and prevent data leakage before it happens.
API call exception monitoring from the perspective of sensitive data
Sensitive data identification is a prerequisite for accurately judging whether API calls will lead to data leakage. Based on the sensitive data identification capabilities of Alibaba Cloud Data Security Center, each API call can clearly see whether sensitive data is involved, preventing leakage incidents. occur.
At the same time, the powerful computing power on the cloud can get rid of the traditional practice of judging abnormalities by rules, and use intelligent models to comprehensively analyze different dimensions such as IP sources, access links, parameters used in the access process, and types of sensitive data obtained, which greatly reduces the False positives and false negatives.
Customer Practice
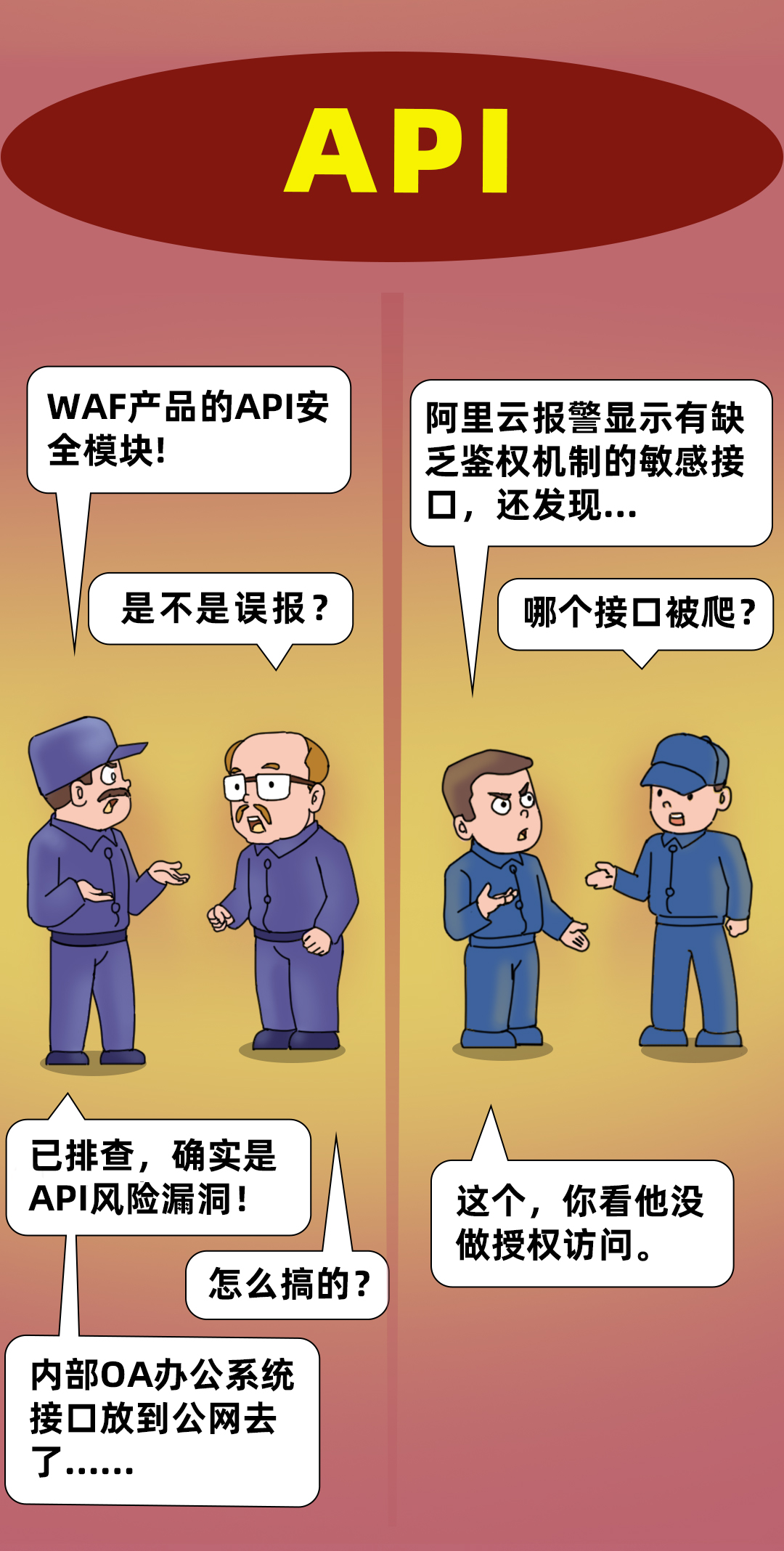
Case 1: A third-party financial software provider, OA system interface public network exposure risk
Ambush hidden danger: The customer has not used effective API management and control tools, and has no understanding of API assets and their protection mechanisms. Moreover, the team's security awareness is weak, and the business side believes that as long as the interface permissions are controlled, there will be no risk even if the API is opened to the public network.
Problems found: By accessing Alibaba Cloud API security products, the customer found that there are tens of thousands of API interfaces, and detected that an employee address book query interface of the OA office system used internally was exposed on the public network and could be accessed without authorization. Through this interface, core sensitive information such as names, contact information, and organizational structure of all employees of the enterprise can be obtained.
After verification, it was confirmed that the customer had API risks, and Alibaba Cloud immediately took security measures:
- Through the WAF console, configure the ACL access whitelist for the API interface (only allow access from its corporate office network IP, and block access from all other IPs);
- The information is notified to the business team responsible for the system for rectification, and the next day the business team fixes the vulnerability of unauthorized access to the interface;
- According to the analysis results of API security, configure ACL access control for all API interfaces used internally by WAF to restrict access sources
Case 2: Unauthorized access to customer consumption information of a catering company
Consumers' names, mobile phone numbers and other information are personal privacy data that the "Personal Information Protection Law" clearly needs to protect, and their consumption data is the core business data of enterprises.
By accessing the Alibaba Cloud API security product, the customer detects that one of its interfaces for querying customer consumption records has unauthorized access. Through this interface, the name, contact information, consumption records, consumption habits, etc. of any customer can be obtained based on the mobile phone number. The core sensitive information of enterprises and customers.
Although the client has consciously protected this part of the data, due to the code logic defect in the interface authentication part, on the surface, the interface request needs to carry the identity field for authentication, but the actual code does not verify this field. This leads to the risk of unauthorized access and unauthorized access to the interface.
After paying attention to the API risk vulnerability alarm and abnormal behavior event alarm, the customer quickly contacted the Alibaba Cloud security team to investigate and confirmed the existence of the API risk vulnerability, and immediately confirmed the attack attribute of the abnormal access behavior. The security team immediately blocked all access to the interface through the WAF console to stop the bleeding urgently, and notified the business team of the system to rectify the information. One week later, the business team fixed the vulnerability, and the interface was re-enabled to provide services. A potential data breach occurred.
Copyright statement: The content of this article is contributed by Alibaba Cloud's real-name registered users. The copyright belongs to the original author. The Alibaba Cloud developer community does not own the copyright and does not assume the corresponding legal responsibility. For specific rules, please refer to the "Alibaba Cloud Developer Community User Service Agreement" and "Alibaba Cloud Developer Community Intellectual Property Protection Guidelines". If you find any content suspected of plagiarism in this community, fill out the infringement complaint form to report it. Once verified, this community will delete the allegedly infringing content immediately.





**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。