This article describes how Apache APISIX integrates with Hydra for centralized authentication.
Background introduction
Apache APISIX
Apache APISIX is an open source cloud-native API gateway. As an API gateway, it has the characteristics of dynamic, real-time, and high performance. It provides load balancing, dynamic upstream, grayscale publishing, service fuse, identity authentication, and observability. traffic management function. You can use APISIX to handle traditional north-south traffic and east-west traffic between services, or it can be used as a K8s ingress controller.
APISIX's OpenID Connect plug-in supports the OpenID Connect protocol. Users can use this plug-in to allow APISIX to connect with many authentication service providers and deploy it in enterprises as a centralized authentication gateway.
Hydra
Ory Hydra is one of the identity providers that supports the OAuth 2.0 and OpenID Connect protocols, based on the OAuth 2.0 authorization framework and the Open ID Connect Core 1.0 framework, with both open source and cloud-native features. It can be integrated with any login system, enabling third parties to easily access your API through OAuth 2.0 Access, Refresh and ID Tokens, enabling users to interact with any application anytime, anywhere.
Ory Hydra is written in Go and provides SDKs for almost all languages, including Dart, .NET, Go, Java, PHP, Python, Ruby, Rust, and Typescript. It works with any login system, and the login experience can be easily customized.
Introduction
OpenID is a centralized authentication mode, which is a decentralized identity authentication system. The advantage of using OpenID is that users only need to register and log in on one OpenID identity provider's website and use one account and password information to access different applications.
The openid-connect plugin supported by APISIX can be integrated with authentication programs that support the OpenID Connect protocol. Like Ory Hydra.
One of the biggest advantages of Ory Hydra is that it implements the OAuth and OpenID Connect standards, rather than forcing you to use "Hydra user management" (login, logout, profile management, registration), a specific template engine, or a predefined front end.
It allows to use the authentication mechanisms required by your program (token-based 2FA, SMS 2FA, etc.) and implement user management and login in your tech stack. Of course you can also use existing solutions like authboss . It gives you all the good features of OAuth 2.0 and OpenID Connect while being minimally intrusive to the business logic and technology stack.
OAuth 2.0 is suitable for a variety of environments and multi-purpose scenarios. The following information may help you determine whether OAuth 2.0 and Hydra are suitable for a certain use case: https://www.ory.sh/docs/hydra
- Allow third-party partners to access your API.
- Become an identity provider like Google, Facebook or Microsoft.
- Enable browsers, mobile devices, or wearable applications to access your API: Running an OAuth2 provider does this well. You don't have to store passwords on your device, and you can revoke access tokens at any time.
- Want to limit the types of information that backend services can read from each other. For example, only the commenting service is allowed to get user profile updates, but not user passwords.
How to do it
Next, I'll show you how APISIX integrates with Hydra using real-world examples. In this example, Docker will be used to run the required environment, please install Docker before performing this operation.
Step 1: Create and run the database
To quickly deploy a test environment, we will use Docker to run PostgreSQL as Hydra's database. It is not recommended to use Docker to run the database in production.
docker network create hydraguide && \
docker run \
--network hydraguide \
--name ory-hydra-example--postgres \
-e POSTGRES_USER=hydra \
-e POSTGRES_PASSWORD=secret \
-e POSTGRES_DB=hydra \
-d postgres:9.6 The above command will create a network named hydraguide and start a Postgres instance named ory-hydra-example--postgres which creates the database hydra , user hydra and user password secret .
Step 2: Deploy Hydra
In this step, 4444 and 4445 will be mapped to 5444 and 5445 .
- System keys can only be set for new databases, and key rotation is not supported. This key is used to encrypt the database and needs to be set to the same value every time the process (re)starts. You can use
/dev/urandomto generate the key. But make sure that the key must be the same when you define it. For example, you can store the value somewhere:
export SECRETS_SYSTEM=$(export LC_CTYPE=C; cat /dev/urandom | tr -dc 'a-zA-Z0-9' | fold -w 32 | head -n 1)Set Hydra's database URL to point to the Postgres instance by configuring environment variables.
export DSN=postgres://hydra:secret@ory-hydra-example--postgres:5432/hydra?sslmode=disable- Ory Hydra does not automatically migrate SQL, so you need to manually migrate the database.
docker pull oryd/hydra:v1.10.6 && \
docker run -it --rm \
--network hydraguide \
oryd/hydra:v1.10.6 \
migrate sql --yes $DSN- Run the Hydra server by the following command. For more information, see deploy-ory-hydra .
docker run -d \
--name ory-hydra-example--hydra \
--network hydraguide \
-p 5444:4444 \
-p 5445:4445 \
-e SECRETS_SYSTEM=$SECRETS_SYSTEM \
-e DSN=$DSN \
-e URLS_SELF_ISSUER=https://localhost:5444/ \
-e URLS_CONSENT=http://localhost:9020/consent \
-e URLS_LOGIN=http://localhost:9020/login \
oryd/hydra:v1.10.6 serve allYou can view Hydra logs with the following command. If you do not specify Hydra's password, you can find relevant information in the log, otherwise Hydra will not be able to restart.
docker logs ory-hydra-example--hydraYou can also use the following commands to view Hydra related introduction and operation commands.
docker run -it --rm --entrypoint hydra oryd/hydra:v1.10.6 help serveStep 3: Deploy login and authentication procedures
Login Provider and Consent Provider can be two separate Web services. Hydra provides sample programs that combine both functions in one application. Next. We will deploy the application using Docker.
docker pull oryd/hydra-login-consent-node:v1.10.6 && \
docker run -d \
--name ory-hydra-example--consent \
-p 9020:3000 \
--network hydraguide \
-e HYDRA_ADMIN_URL=https://ory-hydra-example--hydra:4445 \
-e NODE_TLS_REJECT_UNAUTHORIZED=0 \
oryd/hydra-login-consent-node:v1.10.6You can check if the program is working properly with the following command:
docker logs ory-hydra-example--consentNormal return result:
> hydra-login-consent-logout@0.0.0 serve /usr/src/app
> node lib/app.js
Listening on http://0.0.0.0:3000Step 4: Execute the OAuth 2.0 authorization code flow
Hydra supports the ability to set an OAuth 2.0 consumer and an OAuth 2.0 callback URL via the CLI, typically a third-party application requesting access to user resources on the server.
This information is required to configure the APISIX openid-connect plugin:
-
idcorresponds to the plugin configuration in the following routeclient_id. -
secretcorresponds toclient_secretconfigured by the plugin in the following route. -
scopecorresponds toscopeconfigured by the plugin in the following route.
docker run --rm -it \
-e HYDRA_ADMIN_URL=https://ory-hydra-example--hydra:4445 \
-- network hydraguide \
oryd/hydra:v1.10.6 \
clients create --skip-tls-verify \
--id facebook-photo-backup \
--secret some-secret \
--grant-types authorization_code,refresh_token,client_credentials,implicit \
--response-types token,code,id_token \
--scope openid,offline,photos.read \
--callbacks http://127.0.0.1:9010/callback The following example will perform an OAuth 2.0 authorization flow. To simplify this, the Hydra CLI provides a helper command named hydra token user .
docker run --rm -it \
--network hydraguide \
-p 9010:9010 \
oryd/hydra:v1.10.6 \
token user --skip-tls-verify \
--port 9010 \
--auth-url https://localhost:5444/oauth2/auth \
--token-url https://localhost:5444/oauth2/token \
--client-id facebook-photo-backup \
--client-secret some-secret \
--scope openid,offline,photos.readThe returned result is as follows, indicating that the configuration is normal:
Setting up home route on http://127.0.0.1:9010/
Setting up callback listener on http://127.0.0.1:9010/callback
Press ctrl + c on Linux / Windows or cmd + c on OSX to end the process.
If your browser doesn't open automatically, navigate to:
http://127.0.0.1:9010/Completing this step will launch a user login procedure that we will use in the next step.
Step 5: Start APISIX and configure routing
If you have not installed APISIX, please refer to: Install APISIX .
After the installation is complete, you only need to create a route and configure openid-connect plugin. In order to verify the effect more intuitively, we also need to start an NGINX service as the upstream, you can also use the existing upstream service.
Note: APISIX in this example is installed on the host. If APISIX is started using Docker, network problems may occur.
- First create an NGINX upstream using Docker.
docker run -d --name test-nginx -p 8083:80 nginx- Create a route with the following commands and configure
openid-connectplugin.
Where client_id and client_secret and scope are the IDs set in step 4. You can refer toPreparing for Production for additional information. From the above page, we can see that the address of ---cd55150a864b68af1f0e9ec7e1712dbd discovery is https://{IP:Port}/.well-known/openid-configuration .
curl http://127.0.0.1:9080/apisix/admin/routes/1 \
-H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '
{
"uri":"/*",
"plugins":{
"openid-connect":{
"client_id":"facebook-photo-backup",
"client_secret":"some-secret",
"discovery":"https://127.0.0.1:5444/.well-known/openid-configuration",
"scope":"openid",
"token_endpoint_auth_method": "client_secret_basic",
"bearer_only": false,
"redirect_uri":"http://127.0.0.1:9080/callback"
}
},
"upstream":{
"type":"roundrobin",
"nodes":{
"127.0.0.1:8083":1
}
}
}'Step 6: Access APISIX
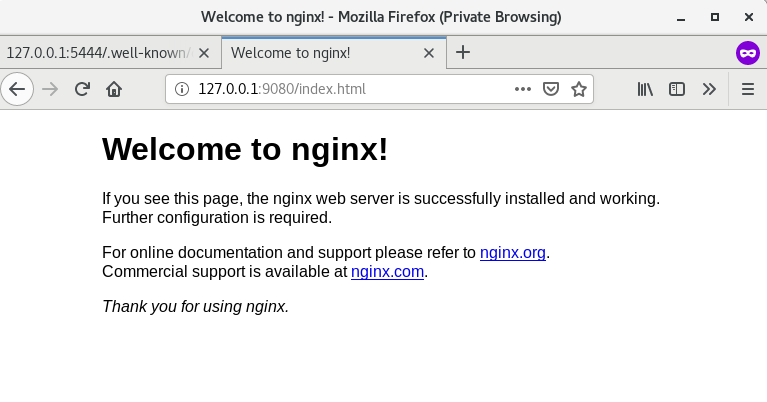
- Enter http://127.0.0.1:9080/index.html in the browser. Since the
openid-connectplugin has been enabled, the page is redirected to the login page. Enter the default account password in the user authentication program.
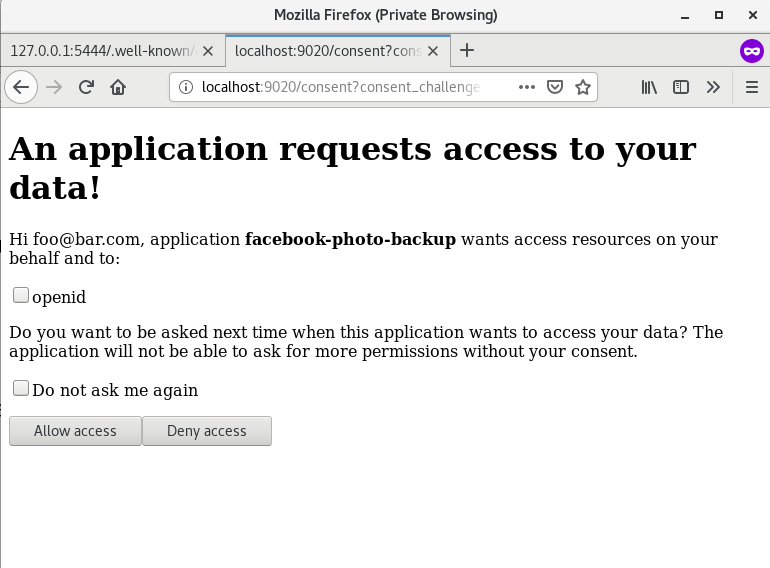
- Select an authentication protocol and allow access.
- After successful login, you can access the page of the upstream service.
Summarize
This article mainly introduces how Hydra integrates with APISIX and the application scenarios of Hydra. You only need to install Hydra-related programs on the server, and you can use it directly as your authentication program. This authentication method reduces learning and maintenance costs, and also provides users with a secure and streamlined experience.
refer to:
https://www.ory.sh/docs/hydra/configure-deploy
https://www.ory.sh/docs/hydra/5min-tutorial
https://www.ory.sh/docs/hydra/install
https://www.ory.sh/docs/hydra/#is-ory-hydra-the-right-fit-for-you

**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。