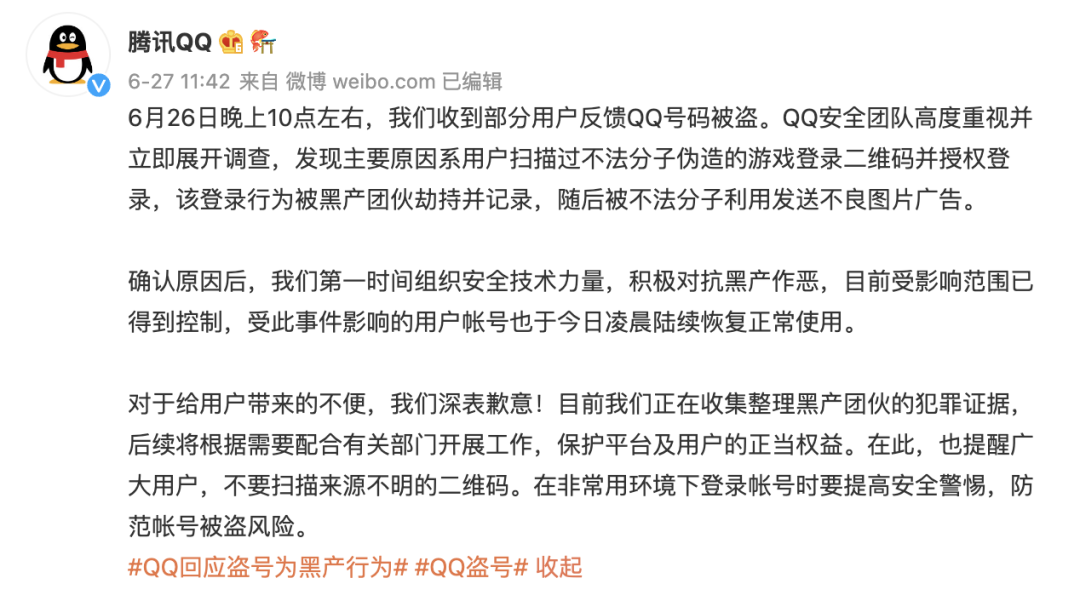
On the evening of June 26, a large number of news about QQ being stolen hit Weibo hot search. Many people reported that their QQ was sending a large number of illegal pictures uncontrollably.
On the morning of June 27, Tencent QQ officially released an announcement.
The announcement concluded that "the user has scanned the QR code for fishing, and it has nothing to do with Tencent".
Is it related to Tencent? Let's analyze the analysis.
Scan code to log in
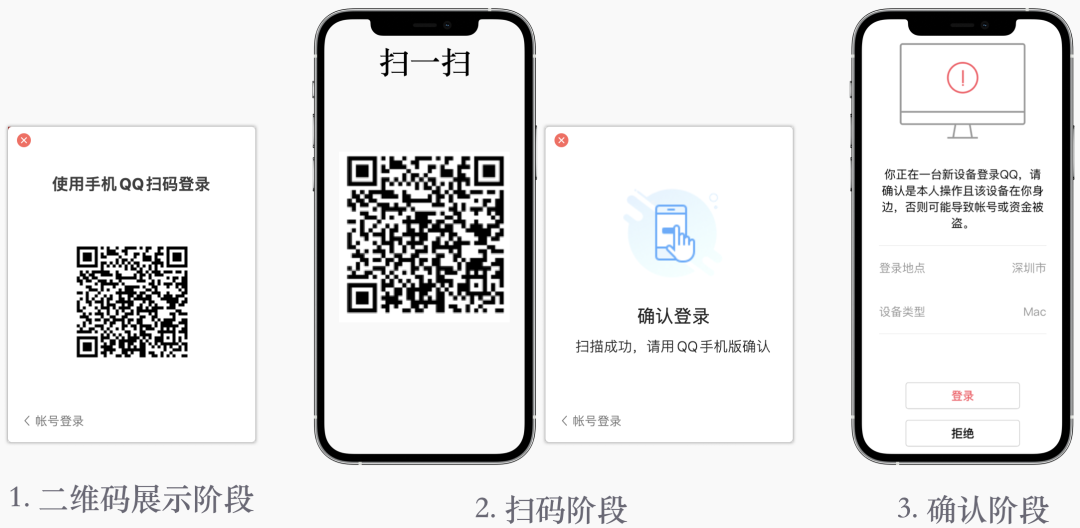
First look at the QQ scan login process, which is roughly divided into three stages:
- QR code display stage
- Scanning stage
- Login confirmation stage
Let's go through the login process briefly:
- The user opens the computer QQ.
- Computer QQ displays a QR code.
- The user picks up the mobile phone and scans the code.
- The computer QQ displays "Scan code is successful, please confirm with QQ mobile version".
- Mobile QQ displays "You are logging in to QQ with a new device", allowing users to choose whether to log in or refuse.
- The user chooses to log in, the computer QQ login is successful, and the whole process ends.
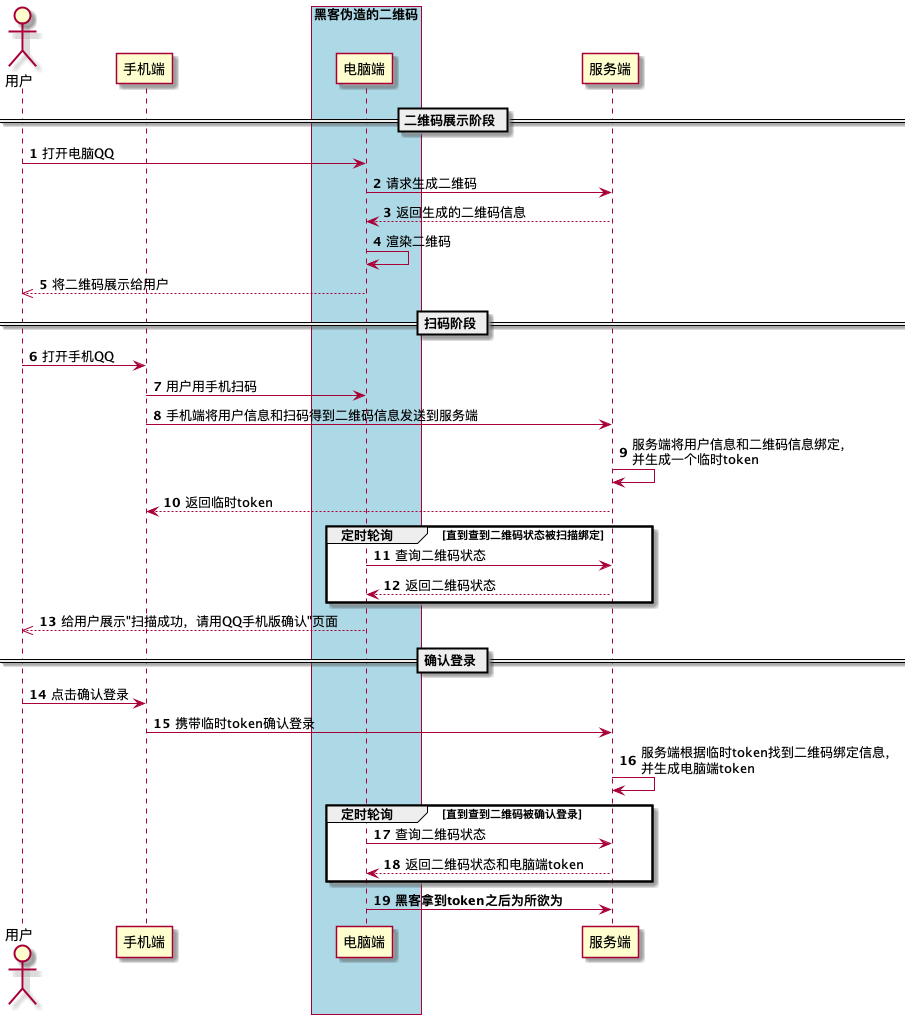
Draw the entire sequence diagram based on the user's behavior:
This scan code login process is widely used in the industry, and it is enough to justify it.
There are four participants in the process, namely: _user_, _mobile phone_, _computer_, _Tencent QQ server_.
Hackers cannot forge users, mobile phones, and Tencent QQ servers, but they can do things on the computer. This is exactly what happened in this account hacking incident.
How was it attacked? Let's look down.
How hackers steal numbers
According to some information I have learned, I boldly guess the process of hacking:
The WeGame in the Internet cafe was injected by the hacker, and then the hacker used the watch QQ login QR code to disguise the WeGame login QR code, hijacking the user's authorization information, and the hacker used the authorization information to interact with the Tencent server and send pictures in batches.
According to my inference, restore the crime scene:
First, hackers invaded a large Internet cafe management service provider and injected a layer of phishing entry into the WeGame software.
Then the Internet cafe under the service provider downloaded the injected WeGame.
Users go to Internet cafes to surf the Internet, and when they open WeGame, they also open the fishing portal.
Entering the account password for this phishing entry shows a login error.
Therefore, the user can only scan the code to log in, but when the user scans it, what he sees is the login watch QQ.
The user was puzzled, but did not think too much, and clicked OK to log in.
The authorization is successful, and the hacker gets the authorization information.
During the whole process, the hacker did not directly steal your account password, but only obtained your authorization information through "phishing".
Tencent's server, on the other hand, only recognizes the authorization information and does not recognize the person. As long as the authorization information is correct, no matter who requests it, Tencent will release it.
In this way, the hacker has gained the trust of the server and let your account send pictures in batches.
Reply
According to the above inference, there will be several problems:
1. Why didn't the people who had been hacked to go offline?
As mentioned above, the hacker obtained the authorization information of watch QQ, and watch QQ does not conflict with mobile phone QQ and computer QQ.
That is to say, even if your mobile phone QQ is online, the hacker can send messages, and even if you withdraw, the hacker can continue to send pictures.
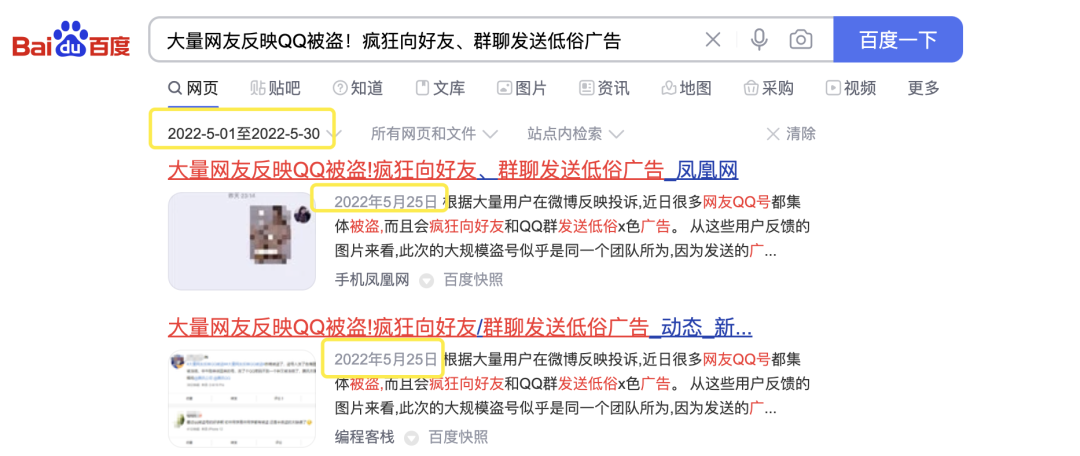
2. Is it the first time that such a large number of hacking incidents have occurred?
no. There was a similar case as early as May, but it looks like Tencent didn't take it seriously.
3. Why is QQ often stolen, but not WeChat?
QQ was born in 1999. It belongs to the product of ancient times, and there are many problems left over from history.
WeChat was born in 2011, skipping some of the pits that QQ stepped on, and its permissions are more strictly controlled.
Although WeChat is not as powerful as QQ in terms of functions, it has always done better than QQ in terms of security. After all, _security_ is the foundation of software with financial attributes such as WeChat and Alipay.
4. Why was QQ stolen without scanning any code? Why is the QQ that has not been used for three hundred years also stolen? Why are some deceased people's QQ also stolen?
If this is the case, then I can't explain it, I can only let Tencent explain.
some other views
The above is what I speculate and deal with based on the information on the Internet, and there are other opinions on the Internet.
The more mainstream ones are "learning information stuffing" and "js hijacking authorization information".
Learn to hit the library
The core of this argument is that Xuetong leaked the user's information, and then some users' Xuetong passwords and QQ passwords were set to be the same, which indirectly led to the leakage of users' QQ passwords.
Personally, I think this possibility is very low.
why?
First, Tencent and Xuetong apps of this size will definitely desensitize and encrypt user passwords, and cannot directly attack credential stuffing.
Second, even if the encryption method is cracked and the user's password is obtained, it is difficult to directly log in to the user's QQ. Because when logging in, the new device login verification will be triggered. If the user's login verification code cannot be obtained, there is no way to log in successfully.
JS gets authorization information
According to Kuan boss @JiuXia2025, a large amount of QQ was stolen this time because the user clicked on a link, and then the cookie in the browser was hijacked by js, and the hacker obtained the key that can control the QQ account. send pictures.
The picture comes from why technology
I have no doubts about the power of the boss.
I remain skeptical about the big guy's point of view.
First, I don't believe that Tencent has not protected against js attacks after so many years.
Second, I don't think that when you click a link in QQ, QQ will authorize the browser to have the permission to "send messages". If there is no "send message" permission, even if the browser's authorization information is hijacked by js, it doesn't make any sense.
Summarize
To sum up my opinion is:
A rich man has too much money and is always stolen, so the rich man spent a lot of money to build the most awesome door in the world. To open the door, he needs to go through 24 organs and five password confirmations. Finally, he needs to verify his fingerprint and password. human face.
Even so, the rich man's money was stolen.
Why is it still stolen?
The reporter interviewed the rich man.
The rich man only said one sentence: all the responsibility lies with the user.
write at the end
Eating melons and eating melons still requires technology. I predict that the process of scanning the code to log in will become a popular interview question in the near future.
why?
First, it can verify whether the candidate has a keen grasp of technology.
Second, it can be well extended to other technical points. for example:
- How to set the expiration time of Redis? Has it been used in the project?
- What is the difference between Token, Cookie, and Session?
- Why poll for QR code status? Can't use Http long connection? Can't use Websocket?
- What other common attack methods? What are the countermeasures?
- Know about OAuth2.0 and JWT?
Look, does this set of punches flow smoothly and in one go?
So, you have to keep learning!
After all, the end of the universe is the king of scrolls, and you don't learn him to be the king.
All the above inferences only represent personal opinions and are personal conjectures, and the materials are all from the Internet.
All are subject to official announcements, do not believe rumors and do not spread rumors.
Welcome to the personal public account [CoderW]



**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。