Every device on the Internet will have an IP address. When we visit a website or send information, we actually make accurate requests through the IP address. But this IP address is made up of a long string of numbers, which is quite difficult to remember, so we created more practical domain names instead of IP addresses. And how the domain name and IP address are linked is where the Domain Name System (DNS) comes into play. It consists of various name servers (that is, DNS servers), which are responsible for domain name resolution and help clients establish connections. It is one of the most important services in the network.
Communication between name servers and clients presents certain security risks, and there are many ways that some malicious people can tamper with name resolution on the Internet. The DNS spoofing discussed in this article is to launch a spoofing attack through a fake IP address.
What is DNS spoofing?
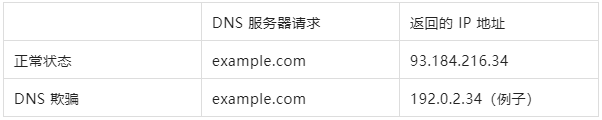
DNS spoofing means that the DNS name resolution is tampered with, and DNS spoofing is particularly prone to forging the IP address of the domain name. This is because DNS resolution is mostly done on internal systems, and the correct domain name is displayed in the browser, so the user usually doesn't notice the tampering. The specific operation is that the malicious person makes the DNS request return a fake IP address, and when the client establishes a connection with the fake IP address, the user will be redirected to the fake server. A simple example:
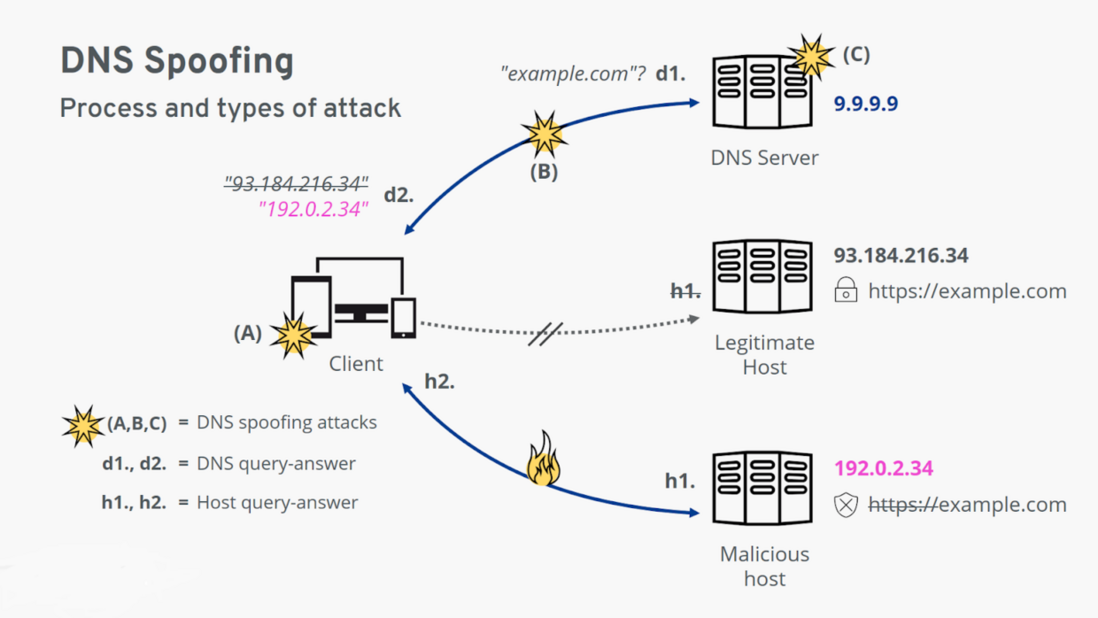
The following figure is a schematic diagram of a case where the client is deceived in the process of connecting to the website example.com:
(The picture comes from the Internet, if there is any infringement, please contact us to delete it)
- d1: The client first requests the IP address of the hostname example.com from the DNS server.
- d2: The client received a response to the request, but it returned a bogus IP address. No connection has been made to the real server for example.com.
- h1: The client sends the request to a malicious host behind a fake IP address.
- h2: A malicious host returns a legitimate-looking website page to the client. However, the security certificate for the domain name is missing on the malicious host.
- A, B, C: These are the different attack points for DNS spoofing: on the client or local router, on the network connection, and on the DNS server.
What threats do DNS spoofing pose?
Attackers use DNS spoofing to conduct phishing and domain spoofing attacks with the goal of intercepting user data on the Internet. Because DNS spoofing affects every connection the client makes. Whether visiting a website or sending an email, if the IP address of the relevant server is tampered with, the purpose is to convince the victim that they have finally accessed a legitimate address, and use the victim's trust to lure malware into downloading and infecting the system, thereby stealing Sensitive user data.
DNS spoofing poses the following risks:
- Confidential data theft: Phishing is used to steal sensitive data such as passwords. These methods are often used to hack into computer systems or to perform various scams.
- System Malware Infection: Victims are tricked into installing malware on their systems, opening the door to further attacks.
- Collection of user data: Personal data is collected in the process, sold or used in other targeted phishing attacks.
- Persistent threat: In DNS spoofing, tampered DNS response information may remain in the cache, spoofing for an extended period of time.
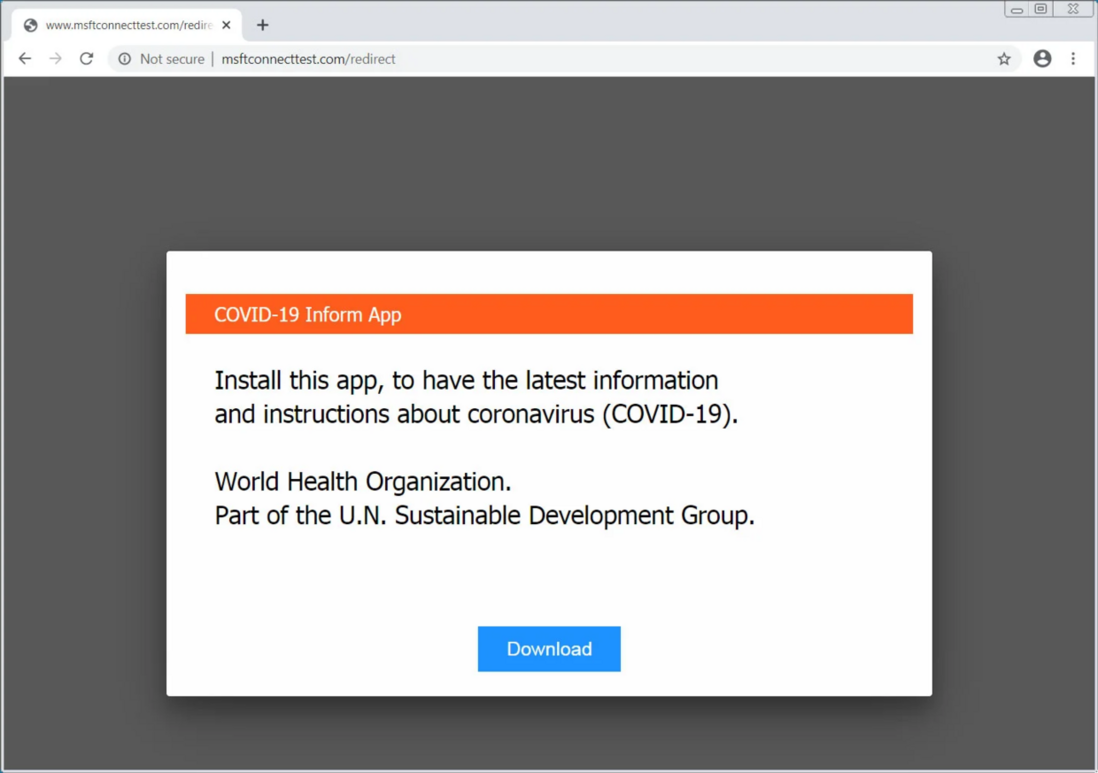
During the COVID-19 epidemic in the spring of 2020, DNS spoofing attacks occurred abroad. The attacker hijacked the router's DNS and tampered with a malicious IP address. Victims' browsers open themselves and display a message prompting them to download a "COVID-19 notification app" purportedly from the World Health Organization (WHO). But in fact, the software is Trojan software. If the victim installs the Trojan software, it searches the local system and tries to access sensitive data, which is used in phishing attacks against the victim.
△ Msftconnecttest page promoting fake COVID-19 information app
DNS spoofing isn't all malicious, though, and some Internet Service Providers (ISPs) occasionally use DNS spoofing to censor or serve ads. For example, ISPs can deliberately manipulate their DNS tables to enforce state censorship requirements. Doing so will prevent users from accessing the offending website, and will be redirected to a warning page when they visit the banned domain. DNS spoofing can also help collect user data or serve ads through redirects. For example, when a user enters a nonexistent or misspelled domain name, ISPs use DNS spoofing to redirect the user to a specific page that may play an advertisement or create a user profile.
How to avoid DNS spoofing?
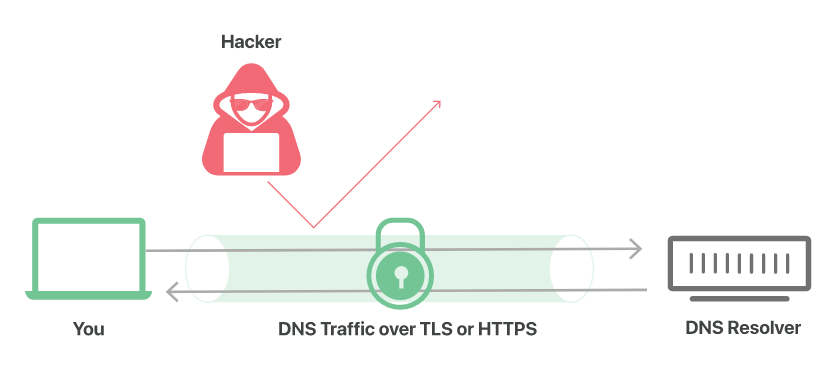
As a type of threat that affects information security, DNS needs to be vigilant against DNS spoofing. We can effectively prevent DNS spoofing by means of encryption measures. Encryption methods generally have two key advantages:
- Protect data from unauthorized access by third parties
- Guarantee the authenticity of both parties
For webmasters, the available encryption methods are to enable mandatory HTTPS for the website domain name, and the connections configured in the email client (eg IMAP, POP3 and SMTP) use the secure protocols TLS and SSL. This type of encryption can protect the data transmission in the request. If an attacker tries to impersonate a normal host, the client will be prompted with a certificate error, reducing the possibility of DNS spoofing.
The connection between DNS servers can also reduce dangerous man-in-the-middle attacks through technologies such as DNSCrypt, DNS over HTTPS (DoH), and DNS over TLS (DoT). However, it should be noted that the application of these three solutions is not very common, and the DNS server must support the corresponding security technology in order to use these three methods for encryption work.
The above mentioned are the encryption methods that administrators can do, and for users, we can use public DNS to avoid DNS spoofing. The setup is very simple, just change the DNS address directly in the system's "Network Settings". In addition to dealing with DNS spoofing, public DNS can also speed up resolution responses. At the same time, large public DNS usually use advanced security technologies such as DNSSEC (DNS Security Extensions), DoH, DoT and DNSCrypt. Common public DNS includes 114.114.114.114 of 114DNS, which is pure and free from hijacking; Google's 8.8.8.8 and Quad9's 9.9.9.9 both support DNSSEC.
This is all about DNS spoofing for the time being. After reading this article, I hope to help you better protect your information security.
Recommended reading
DNS series (1): Why does the updated DNS record not take effect?
DNS series (2): DNS records and how they work, do you understand?

**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。