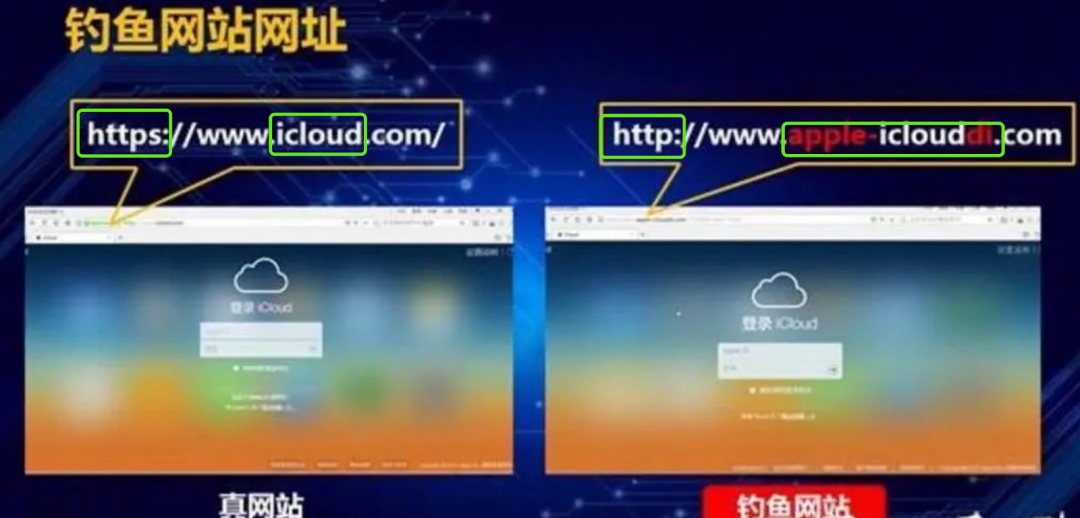
With the rapid development of the Internet, security issues such as user information leakage and data leakage occur frequently. All this is not necessarily a problem with the website, sometimes it may be that you accidentally leak your information. For example, phishing websites are common in daily life. Phishing websites are slightly different from real websites. They generally disguise themselves as banks or other websites to induce users to click and steal private information such as bank account numbers, ID cards, and passwords entered by users. It is difficult for users to distinguish fake websites at the first time, and they will be deceived if they are not careful.
As an enterprise, deploying an SSL certificate can not only help users identify the correct website, but also ensure the secure transmission of website data. So how exactly does an SSL certificate protect website information?
What is an SSL certificate
Before talking about SSL certificates, let's first understand what is the SSL security protocol.
The SSL security protocol was originally designed and developed by Netscape Company in the United States. It constructs a secure channel between the browser and the Web server for data transmission. SSL runs above the TCP/IP layer and below the application layer, using public key technology. The SSL security protocol is mainly used to provide authentication for users and servers, to ensure that data is not changed during transmission, and to ensure data integrity.
An SSL certificate is a digital certificate issued by a trusted digital certificate authority CA after verifying the identity of the server in compliance with the SSL protocol. The SSL certificate contains information such as the domain name of the website, the validity period of the certificate, the issuing authority of the certificate, and the public key used to encrypt the transmission password.
The encryption method of SSL certificates is based on public key infrastructure (PKI) and public key encryption. This method contains two different encryption keys: a private key and a public key, the public key is used for encryption and the private key is used for decryption.
Each user sets a specific private key (private key) known only to him, and uses it to decrypt and sign; Shared by group users, used to encrypt and verify signatures. When sending a confidential document, the sender encrypts the data with the receiver's public key, and the receiver decrypts it with his own private key, so that the information can reach its destination safely and without error.
In simple terms, it allows the server and the client to negotiate the encryption algorithm and encryption key before transmitting application data. The client proposes all encryption algorithms that it can support, and the server selects the algorithm that is most suitable for it.
Deploy SSL certificate
After the website deploys the SSL security certificate, the browser will close the insecure prompt and determine that the website is safe. At the same time, the small lock logo will be displayed, and clicking the small lock will have the relevant information of the certificate, which allows users to identify the security of the website and reduce the interception of phishing websites. In addition, there are many other advantages of deploying SSL certificates for websites. For example: optimizing website search engine ranking, enhancing website image, enhancing customer trust, etc.
It can be seen from this that SSL certificates play an extremely important role in network security, and it has become a general trend to deploy SSL certificates to websites. At the same time, the operation steps of deploying an SSL certificate to a website are very simple. You only need the following three steps to complete:
- Apply for an SSL certificate
- Self-deploy SSL certificate
- Upgrade your website to HTTPS
Youpai Cloud SSL certificate service cooperates with the world's top CA agencies to provide users with a one-stop HTTPS security solution. Users can directly purchase various types of SSL certificates (including two free certificates) in Youpaiyun. When applying, they only need to submit the domain name and fill in the necessary information to complete the certificate purchase.
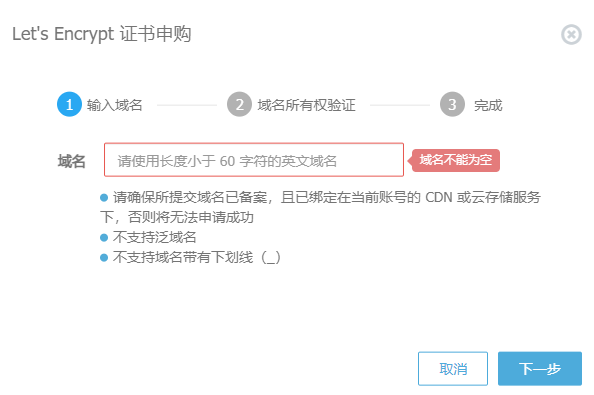
△ Let's Encrypt certificate purchase process example
You can complete the certificate deployment independently without the complicated process of purchasing certificates in Youpaiyun, easily realize the HTTPS encryption deployment of websites and web applications, and quickly escort the enterprise network security.



**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。